Behind the Internet Wheels of Steel - Recording Live From Somewhere - Mixing the Fresh Beats of Technology, Intelligence, Science & Security together with the occasional bass-heavy break of Humor.
"There is no security on this earth, there is only opportunity"
- General Douglas MacArthur (1880-1964)
Wednesday, May 31, 2006
Swedish Government Shuts Down "The Pirate Bay"
In the morning of 2006-05-31 the Swedish National Criminal Police showed a search warrant to RixPort80 personnell. The warrant was valid for all datacentres of RixPort80 and was directed at The Pirate Bay. The allegation was breach of copy-right law, alternatively assisting breach of copy-right law.
I suppose it was only a matter of time.....
Stardust: OpenOffice PoC Virus
Check this SF article for more details.
An unknown virus writer has created the first macro virus that targets computers running the alternative word processors OpenOffice and StarOffice, antivirus firm Kaspersky Labs said on Tuesday.
The virus, which Kaspersky called StarOffice.Stardust.A on its Viruslist blog, is written in StarBasic, a variant of the BASIC programming language designed for scripting common functions in the StarOffice and OpenOffice word processors. While the virus attempts to spread to computers through OpenOffice and StarOffice, Kaspersky called the functionality theoretical.
Tuesday, May 30, 2006
Fun: Recently Unearthed E-Mail Reveals What Life Was Like In 1995
Sunday, May 28, 2006
THC Courts Phone Hackers
Posted on THC.org by DerSteppenwolf :
THC is the world's first group to release ROM images and memory maps from Nokia Mobile Phones. This is an invitation for Reverse Engineers and hackers to discover hidden secrets and backdoors on mobile phones.
http://thc.org/thc-rom/
The Perfect Recipe for Defacement
It appears that Turkey as a whole isn't letting up on the defacements. They can account for over half of all the defacements tracked by Zone-H.org - taking the spot from Brazil just recently.
Recent Turkish Defacements
aLpTurkTegin - http://woodlandsperfumers.com/
SanalYargic - http://grupocastor.com.uy/portal/index.php
TurkStorm.Org - http://www.progtv.be/
yusufislam - http://gladtidingsofduluth.org/forum/
narcotic - http://upload.neuper-team.com/index.html
The list goes on and on....
The Internet Storm Center is already reporting a possible "script kiddie contest" underway. Crazy kids.
Looks like alot of the defacements are caused by PHP security issues.
Saturday, May 27, 2006
BackTrack 1.0 Final Released
If you are still using Security Auditor or WHAX, then catch up with the times and get the new BackTrack...you will be glad you did.
Apple Failed in Battle to Slient the "Media"
Charles Cooper has a great article over at CNet.com -
Hopefully Apple is making an effort to find the leaks inside, instead of just pulling the A-team of lawyers out at the drop of a hat.
Friday, May 26, 2006
Microsoft Word Unspecified Remote Code Execution - UPDATED
Most of the antispyware friends that I talked to have samples and didn't really see anything different than has already been reported. But it did take a while for everyone to get a sample, this shows just how rare it is in the wild.
I have a sample as well, but haven't had a chance to look at it. I have almost zero RCE skills, so I don't think having a sample is going to help me understand it much better.
The first attack was very limited in scope and Microsoft appears to be doing the right think and will not jump the gun to release a patch early. Some people are giving them hell about that, but I don't see a real reason for them to rush it at this point - in this exact case.
In some cases, it doesn't make sense to hold the patch until Patch Tuesday.
If the vulnerable function is known and being exploited in the public, then the patch should be released as soon as it is ready. Releasing it early in this current case, will expose the true vulnerability to groups that may not have it now, and in the end this will only increase the number of active exploits against this vector.
SANS - http://isc.sans.org/diary.php?storyid=1345
Microsoft - http://www.microsoft.com/technet/security/advisory/919637.mspx
Blah: Long Weekend
It is amazing the see how empty the Houston airport can be on a Friday night. All the shops are closed and my ice latte is all watered down now. I suppose it is time to break out the redbull and security books until my flight.
Everyone have a great holiday weekend and don't get into too much trouble.
For your weekend reading, check up on the new Norton Corporate Anti-virus hole discovered by eEye and read about this special ring-tone used by teenagers in class.
Wednesday, May 24, 2006
ScanDoo Beta - Making Searching Safe
It is called ScanDoo.
Scandoo is based on ScanSafe’s web security technology that currently scans billions of web requests for corporate employees around the world. ScanSafe software developers were often asked by their friends and family if they could protect home Internet use in the same way that they protect corporate users. When our lab came up with safe searching technology we thought it was such a good idea that we wanted to make it available to all.
When you search in Scandoo, each site is compared to the ScanSafe's database and given an icon.
- Green Check is safe
- Yellow is a warning
- Red is bad
- Black Bug is totally unsafe - known website that contains malware or evil script
This is a great idea for those people that search at work...and don't want the proxy admin at their desk ;)
Tuesday, May 23, 2006
Veterans Affairs Department- data on millions of veterans stolen
The Veterans Affairs Department today revealed that personal, identifying data for as many as 26 million American veterans was stolen from a VA employee's home in May. The information is a list of all veterans who served in the military and were discharged since 1975. A VA employee took files home as part of department work on a data collation project to simplify some VA processes. Subsequently, someone broke into the employee’s home and stole the data. The career employee, a data analyst, was not authorized to take the files home, said VA secretary Jim Nicholson in a teleconference with reporters. He would not say what form the data was in.
I am going to guess and say CSV. ;)
In light of this news, William Jackson wrote a pretty good little article over at GCN.com as well. It is just a reminder that we aren't just holding a PC in our hands, we are holding data that other people might want.
Sunday, May 21, 2006
Google Summer of Code 2006
While it is impossible to talk about all the possible projects, here are a couple of ideas from a couple of the project. Remember, these are just ideas. Students are welcome to submit original ideas and we will see some of those when the dust settles.
Apache SoC 2006
Mozilla SoC 2006
FreeBSD SoC 2006
My coding skillz are very very far from Kung Foo level, but I just might apply for this project idea suggested for Nmap SoC 2006:
------------------------
Slacker
Nmap developers are known as some of the most productive in the open source world. In order to crank out more code, many eschew luxuries like classes, social lives, sex, and sleep. To counterbalance all of this planned productivity, we may need some experienced slackers to spend the summer playing video games, watching TV, reading Slashdot, and dating. You will report these activities in a weekly status report so the rest of us can live our lives vicariously through yours.
Since lazyness is a virtue for this position, our normal application form is not required. Just tell us your best time-wasting story or any other relevant credentials for this critical role.
------------------------
In 2005, there were around 43 mentoring groups signed up for the Summer of Code.
This year they have over 100.
This fall, we should see a ton of great enchancements and new features created by the community for the community. Open source, it is a good thing....
Saturday, May 20, 2006
New Computer Laws - Are they too Broad?
There are hard questions and I don't have all the answer, but here are same of my thoughts on the issue.
1) Dual-Edged Sword - The tricks, skills and tools of the IT security world are commonly called dual-edged swords. Security tools are just that - tools, no different than a gun, a sword, a hammer or a butter knife. We deal with these pretty good in the real world. Cops don't go out into the woods and arrest hunters because they are carrying shotguns. Do they? Intent and context are the true factors that give the law weight. Exploits, like guns, can be used to break into a network...but that same exploit can be used by a security network admin to find a vulnerable server on the network and as a result jump start the protection process.
2) The Grey World - For a long time, I have talked with my friends about the balance of the force in the world. People have the ability to be good or bad, tools have the ability to be used for good or bad. The world truly is Yin and Yang. I am a huge believer in maintaining the balance. Most of the governments in the world are based on the idea and will fail to function without it. If the balance is not maintained, then things start to function in ways that are not desired - Absolute power corrupts absolutely.
So how do we as a world, apply the black & white letters of the law to a world of grey? Very carefully, that is how. It is like a never ending dance...ever changing, ever shaping. What is illegal today could be legal tomorrow...and vice vera. This idea seems very simple when applied to the real world...but it becomes much more cloudy when applied to the virtual world.
We are seeing just how cloudly with these new bills:
1) Possible Update to the UK Computer Misuse Act (CMA)
2) Truth in Caller ID Act of 2006 - this one is pretty good since this trick rarely needed beyond law enforcement....that assumes I am ok with PI's tricking people..umm...I guess so.
4) UK RIP Act - forcing people to hang over encryption keys....
So how do we make objective laws that take into account subjective intent and context? That is a question for the ages, I think.
Friday, May 19, 2006
Microsoft Word Unspecified Remote Code Execution
Symantec has tagged the new backdoor as Backdoor.Ginwui. Norton detects the dropped trojan as Trojan.Mdropper.H - but this is expected to change in my view. This dropped trojan could be replaced in the future with a new altered trojan that is not detected.
Some people are using the term 0-day, but until more information is known, I don't want to use that.
Remember that Microsoft patched several Office remote code execution bugs in MS06-012.
Thursday, May 18, 2006
Fun: 48-Hour Internet Outage Plunges Nation Into Productivity
BOSTON—An Internet worm that disabled networks across the U.S. Monday and Tuesday temporarily thrust the nation into its most severe maelstrom of productivity since 1992.
"In all my years, I've never seen anything like this," said Price Stern Sloan system administrator Andrew Walton, whose effort to restore web service to his company's network was repeatedly hampered by employees busily working at their computers. "The local-access network is functioning, so people can transfer work projects to one another, but there's no e-mail, no eBay, no flaminglips.com. It's pretty much every office worker's worst nightmare."
According to Samuel Kessler, senior director at Symantec, which makes the popular Norton Antivirus software, the Internet "basically collapsed" Monday at 8:34 a.m. EST.
The Gibe-F worm, an e-mail-transmittable virus, initiated cascading server failures. Within an hour, Internet service to more than 90 percent of the U.S. was disabled, either by the worm or by network firewalls that initiated security protocols.
"Unlike SoBig or Blaster, this worm didn't harm individual computers; it just used them as a gate to attack the Internet at the ISP level," Kessler said. "Computer technicians at most offices couldn't do anything but sit by helplessly as people worked through stacks of filing, wrote business-related letters they'd put off for months, and sold record amounts of goods and services over the phone."
Wednesday, May 17, 2006
BackTrack Live CD: Pre-Release Beta Preview
After booting up and looking over the tools quickly, here is what I have.
Kernel – Linux Slax 2.6.15.6
Firefox – 1.5.0.3
Nmap – 4.03
KDE – 3.5.0

There were several tools that were not totally up-to-date, like Ethereal, but I assume there will be another tool update before the finally release. It looks like they were right in the middle of a tool upgrade, I saw several version of John the Ripper and a couple of other tools. I did notice the new Metasploit 3 Alpaha in there as well. ;)


All the normal tools are included. Anyone that has used Backtrack before knows the list is huge, so I won’t even attempt to do that, but if you haven’t see the list – check it.

The new wireless driver switcher is pretty cool as well.
Nice work to the Remote-exploit.org team and all the testers.
I have to run back to work, but look for the new release really really soon.
Apple Releases a Whopping 43 Security Updates
Apple last week released a massive security update package for their Mac OS X operating system as well as updates for the QuickTime player bundled with Mac OS X. The update fixes a number of security issues including a number of code execution vulnerabilities that could allow an attacker to compromise Mac OS X and run undesirable programs.
The update also includes fixes for Apples popular Quick Time player that could allow an attacker to use malformed media files launch denial of service attacks or compromise a users system. The update to QuickTime also improves the applications stability.
The Mac OS X update also fixes code execution vulnerabilities in AppKit, ImageIO, BOM, CFNetwork, ClamAV, CoreFoundation, Finder, FTPServer, FlashPlayer, LaunchServices, libcurl, Preview, QuickDraw and QuickTime Streaming Server.
Anyone have a breakdown on the time between fixes in the open source world and when they are fixed in OS X??
ClamAV and several of the other products are open source, and it is well known that vulnerabilities found in open source products are also found in their OS X couterparts.
This fact isn't something that Apple can afford to overlook. When open source products are patched, the details are handed to the bad guys. How long will that vulnerability exist in OS X before it is fixed??
When Spammers Hit Back
Perhaps one day, the Can-Spam Act can be used to fight the real spam problem, at this point it is just a sheet of paper in my view. Used against real companies that make mistakes, it isn't stopping PharmaMaster and others like him.
------------------------------
Starting May 2, a spammer known as PharmaMaster used a massive network of zombie computers to flood Blue Security's database servers with fake traffic and hijacked a little-known Cisco Systems router feature known as "blackhole filtering" to block anyone outside Israel from accessing Blue Security's homepage.
Blogging software provider Movable Type's hosted service, TypePad, also fell victim to PharmaMaster's bot network, after Blue Security realized that no one could reach its homepage and posted a message to its users on its old blog. Thirty minutes later, PharmaMaster started an attack that brought down thousands of blogs.
Tuesday, May 16, 2006
Myspace Phishing Attacks on the Rise
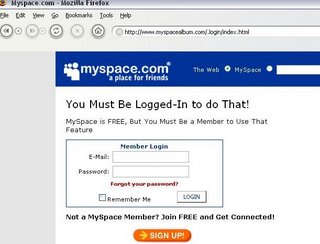
Phishing Attacks against the very popular social networking website are on the rise.
Newest one discovered - http://www[dot]myspacealbum[dot]com/.login/index.html
Abuse Contact @ the Domain has been alerted by e-mail.
This URL was passed around in a bulletin titled "CHECK OUT these old school pictures...". The bulletin was posted by a friend without his knowledge.
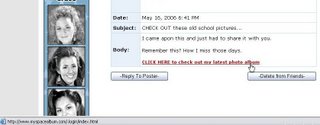
Malware or some type of script injection attack might be the bulletin posting vector.
But if they can send bulletins as you without your knowledge, then can install a bank info stealing trojan with a IE vulnerability. The malware or attack script could alter your profile enough that all visitors (your friends) get attacked via drive-by-install.
Within the past week, another bulletin about "party pictures" was used to spread another phishing URL.
Perhaps Myspace should use some of those ad dollars and think about getting a security@myspace email account working ;)
The collected e-mails and passwords could be used to collect more important information. Tons of people use the same password for both for multiple pages.
Lets just hope that most of the younger people don't have paypal accounts ;)
As these social network groups grow, they are now in the crosshairs to become a future attack vector.
Malware distributors can operate hidden behind the cloak of "fun harmless social interaction" and take advantage of client-side vulnerabilities via script injection - Myspace worm ring a bell.
Sun to Open Source Java
SAN FRANCISCO -- Sun Microsystems Inc. at its JavaOne conference today announced plans to open source Java, but said before it does so company officials have to be certain the move won't lead to diverging paths in the code.
Richard Green, Sun's executive vice president of software, made it absolutely clear that Java would be opened source.
Very interesting but not totally shocking. Sun already has plans to move Solaris totally into the open source model. OpenSolaris.org was opened and already has working open source OS.
In the end, it will be kinda like the Fedora project before the Fedora Foundation was created =)
Perhaps Sun sees that the open source model is the only way to stay in the fight ;)
Sunday, May 14, 2006
Fun: Happy Mothers Day
happy mothers day
Morse Code:
.... .- .--. .--. -.-- -- --- - .... . .-. ... -.. .- -.--
Leet Speak:
h4ppy m07h3r5 d4y
Hex Encoded:
68 61 70 70 79 20 6d 6f 74 68 65 72 73 20 64 61 79
Binary Encoded:
01101000 01100001 01110000 01110000 01111001 00100000 01101101 01101111 01110100 01101000 01100101 01110010 01110011 00100000 01100100 01100001 01111001
Octal Encoded:
150141160160171040155157164150145162163040144141171
Base64 Encoded:
aGFwcHkgbW90aGVycyBkYXk=
ROT13 Encoded:
unccl zbguref qnl
DES Encrypted Using the Phase "candy":
8cIWUhWVxn5iGO1OmCTuFjsC9I9eXUuF
Politicians Target Social Sites For Restrictions
"Politicians are looking for reasons to convince citizens to vote in November, and polls say suburban parents are worried about the internet. Wednesday top House Republicans announced a bill to make 'social' Web sites unreachable from schools and libraries. The bill is intended to go after MySpace, but the actual text of the legislation covers sites that let users 'create profiles' and have a 'forum' for conversations -- which would include Slashdot and many blog sites. House Speaker Dennis Hastert claims it's necessary to stop 'dangerous predators' out here on the Interweb."
I don't like the sound of that at all. Schools should have the power to block whatever you want to protect the student and their network, but this bill sounds way too wide. CNET allows a forum to talk about articles? Will that be blocked? Google has groups, will that make all of Google blocked? Slashdot itself might even be blocked.
IMHO, this will not help anything anyways. Students of this generation are very tech smart, perhaps smarter than the people that are passing the laws. Most students can bypass school proxy systems already very easily. There are whole teen groups and sites dedicated to sharing bypass information. So what is this going to do?? Really?
System Virginity Verifier (SVV) Code Released
Dave Aitel stated that he would work the code into CANVAS - so that each new node could be checked for previous pwners =) Damn cool.
BTW, Happy 30th B-day Dave.
Saturday, May 13, 2006
Fun: Today's Acquisitions
Inside Threat - Designer Virus?
I found this article over at CRN.com.au about a pretty silly virus, but there are notes in the article that point to it being a real life digital designer virus. Even if it was some kid working at BestBuy....
Interesting stuff.
Automated Malware Classification
The company unveiled its plans at the EICAR (European Institute for Computer Anti-Virus Research) conference in Hamburg, Germany, proposing the use of distance measure and machine learning technologies to come up with automatic classification of viruses, Trojans, spyware, rootkits and other malicious software programs.
A research paper presented by Microsoft's lead anti-virus researcher, Tony Lee, described the existing process of manual human malware analysis as "inefficient and inadequate" and suggested an ambitious method that combines runtime behavior analysis, static binary analysis and adaptable algorithms to automate classification.
See the full Microsoft white paper in .DOC form.
Thursday, May 11, 2006
Tools of the Trade - Update
They have also released a Windows setup bundle. It takes care of the Winpcap install, the registry changes and everything for you. Sig DB has increased as well. Go get it.
2) THC has updated Hydra to 5.3 - They added a HTTP form module and NTLM support for pop3, imap, smtp-auth and http-proxy. Very cool.
Brutus has a pretty advanced form module that learns the parameters from the page itself, but it lacks a directory input field for HTTP auth attacks - which is a very nice feature of Hydra.
3) Ethereal 0.99.0 was released out of development. Too many fixes to count. Check out the changelog.
Tuesday, May 9, 2006
Network Neutrality - Money Can't Buy Love
Annalee Newitz said it better than I could myself in her recent column.
Although never written into US law, this principle holds that nobody's Internet traffic should be privileged over anybody else's -- to do so would be like letting an electricity company cut a deal with GE so that only GE appliances got good current. As it turns out, the neutral network provides an excellent platform for business models that cluster at the ends of the wires: Everything from Google and eBay to ISPs and music-downloading companies are based on the idea that money is made by shooting good stuff over the wires, not by making some wires better at getting good stuff.
Well said indeed. Lets show them that no amount of money can take the internet away from us.
Ethics, Hacking and Religion
This hits upon the idea that I talk about once in a while.
Morally right does not always equal legally right; Morally wrong does not always equal legally wrong.
This is the truth that is created by applying black&white rules to a very grey world.
This article brings up a very good view that I haven't seen talked about before now. Very interesting.
I like this quote from Johnny Long - "I felt like God wasn't on the Internet."
Personally I feel we fall into the Yin/Yang world. The world of balance. But I won't go into my balance speech now. lol
Monday, May 8, 2006
Geek vs Nerds
Pundits and observers dispute the relationship of the terms nerd and geek to one another. Some view the geek as a less technically skilled nerd. Some factions maintain that "nerds" have both technical skills and social competence, whereas geeks display technical skills while socially incompetent; others hold an exactly reversed view, with geek serving as the socially competent counterpart of the socially incompetent nerd, and call themselves geeks with pride (compare Geekcorps, an organization that sends people with technical skills to developing countries to assist in computer infrastructure development). Another view is that "geeks" lack both social competency and technical skills. Arguably, a nerd is a more self-controlled sort of person, while a geek can be something of a loose cannon--or at least more awkward in an obstructive way than a nerd.
Everyone knows that geeks are way cooler than nerds....come on!
Vulnerability Disclosure - Moving Toward the Event Horizon
Why is this happening? Lets look at several points then will help paint scene:
1) More and More independent security researchers are getting into legal trouble
I won't sit here and defend people that break the law to show that a piece of software is vulnerable, but where is the line? What is breaking the law and what is not? Security researchers are normal people and like normal people, some are seen socially as good (whitehats) and some are seen socially as bad (blackhats).
Abraham Lincoln once said,
"Discourage litigation. Persuade your neighbors to compromise whenever you can. As a peacemaker the lawyer has superior opportunity of being a good man. There will still be business enough.”
2) It is easier to catch the bass, than the shark - The real evil people in the world are very hard to catch. They are smart, silent and very well organized.
Example 1 -
- Caught - Eric McCarty was arrested after indirectly reporting a vulnerability in a USC student database. He conducted the "attack" from his house and used minimal effort to "cloak" himself. He didn't sell the information to Russian or to a carding crew.
- Not Caught - For two weeks, some people "in Asia" who have been illegally accessing information on 200,000 people at the University of Texas. What are they doing with it? Who knows? Will they be caught? Very unlikely.
Example 2 -
- Caught - William Genovese A.K.A. illwill turned himself in for selling Windows source code for $40. Let’s remember, that the source code was already on P2P and anyone could download it at that point. He did break the law by selling it, no contest with that...but he didn't steal it. It is clear that his punishment was based on past events.
- Not Caught - The person that really stole the code. I guess Microsoft wasn't on the FD security list in 2004. Where are these guys? Microsoft isn't after the real people? It is funny how they fail to note that illwill didn't sell the code when they talk about the arrest in the press. SecurityFocus is one of the few articles that showed the other side.
3) Money moves the world - Even if independent researchers do find problems in Microsoft products, what do they get? They could just pass the vulnerability information on to a third-party and perhaps get a little money out of the deal. What is wrong with that? At least Mozilla gives something back to researchers that report security problems.
4) Big Vendors are hiding vulnerability information - Apple and Microsoft fix more vulnerabilities than are commonly known. They secretly fix security problems in patches and never tell you. But once the patches are released, the bad guys know about these unreported security issues. IDS are slow to catch these issues, because of the reverse engineering time needed to provide protection.
In the end, this all adds up to the public being exposed to less and less vulnerability information.
Sunday, May 7, 2006
Pfizer accused of testing drug on children
A panel of Nigerian medical experts has concluded that the world's largest pharmaceutical company, Pfizer, violated international law by testing an unapproved drug on children with brain infections at a field hospital.
Real Life "Constant Gardener" anyone?
CCTV Planning Documentary on Fall of America
Via the China Confidential Blog -
A China Central Television (CCTV) unit is developing an epic, fall-of-Rome-flavored documentary TV series around the theme of America in decline.
Unlike the crude state-sponsored videos that glorified the September 11 terrorist attacks as a humiliating strike against an arrogant superpower, the planned multipart production promises to be a slick dissection of American economic and military might.
Production notes for the CCTV series, which is tentatively scheduled to air in 2007, are said to provide a revealing glimpse of how certain government officials see the US--namely, as a dying hegemon. The Chinese view is that a number of factors, including "structural" economic problems and imperial overstretch, are combining to end US global supremacy.
In an effort to support and promote this point of view, the CCTV documentary plans to cover all the bases, to use an old American expression borrowed from baseball.
For example, the producers plan to devote at least one episode to the US immigration crisis and attempt to draw historical parallels between a commonly perceived cause of the fall of ancient Rome--unchecked immigration and invasions--and the flood of illegal immigrants pouring into the United States from Mexico and Latin America.
In an ironic twist, the segments on the US economy will supposedly highlight the gloom-and-doom opinions of some smart, successful citizens--fund managers, investment bankers, and analysts--who argue that the country has entered a long period of decline, an economic twilight of sorts, from which no escape is realistically possible. The talking heads of finance are expected to make the case for aggressively investing in emerging markets, especially the so-called BRIC countries (Brazil, Russia, India, China) that are destined to dominate the global economy by 2050, according to an increasingly fashionable Wall Street concept. The CCTV documentary intends to contrast the US financial community's seemingly boundless enthusiasm for investing in China and other emerging markets with an apparently deepening disinterest in domestic investments (except for some stocks, prime property deals and a relative handful of healthcare and high-technology ventures).
The segments on US military power are likely to play up the hoary Mao-era "paper tiger" propaganda line, but with much more finesse than the above-mentioned anti-American videos. Highlighting mistakes made by the Pentagon in Afghanistan and Iraq, the production is expected to make the point that despite its awesome destructive power and global reach, the US military is increasingly overextended and incapable of swift, decisive action around the world. Besides, the documentary is expected to argue, the Iraq experience shows that the American people have lost their taste for foreign intervention and prolonged overseas conflict.
Translation: the US will be in no position to stop China if/when the time comes for it to invade and conquer Taiwan.
Friday, May 5, 2006
Science: Ensign, Engage the Cloak!!
Did you ever play with a tuning fork when you were little? You hit it against the table and then hold it up to a wine glass....the wine glass would match the tuning fork. Pretty cool.
What if we made a light tuning fork? Read on...
Thursday, May 4, 2006
Gone in 20 Minutes: Using Laptops to Steal Cars
High-tech thieves are becoming increasingly savvy when it comes to stealing automobiles equipped with keyless entry and ignition systems. While many computer-based security systems on automobiles require some type of key — mechanical or otherwise — to start the engine, so-called ‘keyless’ setups require only the presence of a key fob to start the engine.
The expert gang suspected of stealing two of David Beckham’s BMW X5 SUVs in the last six months did so by using software programs on a laptop to wirelessly break into the car’s computer, open the doors, and start the engine.
I guess this shouldn't surprise me. As software moves more and more into other parts of our lives, we will see things get hacked that were once only in the hardware hacking world.
Tuesday, May 2, 2006
Water in my Pocket - Nanoelectronics
A team of experimentalists and theorists at the University of Pennsylvania, Drexel University and Harvard University has proposed a new and surprisingly effective means of stabilizing and controlling ferroelectricity in nanostructures: terminating their surfaces with fragments of water. Ferroelectrics are technologically important "smart" materials for many applications because they have local dipoles, which can switch up and down to encode and store information. The team's work is reported in the April issue of Nano Letters.
Wow that is pretty cool, so when can I get my water filled NanoUSB??