Behind the Internet Wheels of Steel - Recording Live From Somewhere - Mixing the Fresh Beats of Technology, Intelligence, Science & Security together with the occasional bass-heavy break of Humor.
"There is no security on this earth, there is only opportunity"
- General Douglas MacArthur (1880-1964)
Thursday, November 30, 2006
Happy Computer Security Day!
http://www.computersecurityday.org/
YEA!!! WOOHHOOO!
Ok, back to work.
Wednesday, November 29, 2006
Adobe ActiveX Control Remote Code Execution Vulnerability
It currently affects the following products:
Adobe Reader versions 7.0.0 through 7.0.8
Adobe Acrobat Standard versions 7.0.0 through 7.0.8
Adobe Acrobat Professional versions 7.0.0 through 7.0.8
The Adobe secuirty team is looking into the issue and currently there is no patch.
Set a kill bit for the CLSID {CA8A9780-280D-11CF-A24D-444553540000} or delete "AcroPDF.dll" will fix the issue for now however.
Adobe -http://www.adobe.com/support/security/advisories/apsa06-02.html
FrSIRT -http://www.frsirt.com/english/advisories/2006/4751
UK Police Ground Airliners For Radiation Testing
Authorities grounded three British Airways jetliners in London and Moscow on Wednesday and drew up plans to contact thousands of airplane passengers as they broadened their investigation into the radiation poisoning death of a former Russian spy.
Two planes at London's Heathrow Airport tested positive for traces of radiation, a third plane has been taken out of service in Moscow awaiting examination.
Home Secretary John Reid disclosed the search following a meeting with COBRA, the government's emergency committee. Reid said two planes had been tested so far and that another would be tested.
The initial results of the forensic tests had shown very low traces of a radioactive substance onboard two aircraft, British Airways said in a statement.
The company added that the investigation is confined to the three planes, which will remain out of service until further notice.
High doses of polonium-210 -- a rare radioactive element usually manufactured in specialized nuclear facilities -- were found in Alexander Litvinenko's body, and traces of radiation have been found at sites in London connected with the investigation of his death.
The airline said it was contacted by the British government late on Tuesday and told to ground the planes, and allow investigators looking into the death of the former intelligence agent to test them for radiation.
All three planes had been on the London-Moscow route, British Airways said. In the last three weeks the planes had also traveled to routes across Europe including Barcelona, Frankfurt and Athens. Around 30,000 passengers had traveled on 220 flights on those planes, said Kate Gay, a spokeswoman for the airline.
"The airline is in the process of making contact with customers who have traveled on flights operated by these aircraft, which operate within Europe," British Airways said in a statement, adding the risk to the public was low.
British Airways website states that three Boeing 767 short haul airliners are currently grounded and under forensic examination.
Researcher Cancels Week of Oracle Database Bugs
Security researcher Ceasar Cerrudo, with the Argentinean security vendor Argeniss, has abandoned his plan for 'a week of Oracle Database Bugs'.
The security vendor was originally planning to release details of an unpatched vulnerability in the Oracle database every day for a period of one week. The event was intended to demonstrate the poor level of security in Oracle's database.
"We have 0-days [zero-day bugs] for all database software vendors but Oracle is "The #1 Star" when talking about lots of unpatched vulnerabilities and not caring about security," the company originally said on its website.
The page was updated on Tuesday. The original text was struck out and above it a notice explained that the event was suspended "due to many problems". The company declined to comment further.
Publishing details of security vulnerabilities before a vendor has released a patch is considered not-done in the security sector because it can put end users at risk.
Late on Monday Oracle published a posting on its security blog lashing out against researchers who published details of so-called 0-day vulnerabilities. The vendor also said that it won't credit researchers in the patch documentation if they prematurely disclose vulnerability details of the flaws they discover. Security researchers generally rely on company credits to market their skills.
Although the posting did not mention Argeniss, it claims to respond to "a flurry of articles and blog entries".
Tuesday, November 28, 2006
UK MoD Conducts Semi-Mock Swarm UAV Test
A jet airliner was flown over south-west England recently with no pilot in the cockpit, to test technology that might one day be used to control swarms of unpiloted aircraft from a single fighter jet.
The two-hour flight, conducted by the UK Ministry of Defence (MoD) and UK defence firm Qinetiq on 30 October 2006, was designed to assess whether a fighter pilot could someday control several uncrewed air vehicles (UAVs) from their own plane.
"The big burning question at the MoD is how to operate UAVs in attack missions in the future," says Kevin Williams, project manager at Qinetiq. "We wanted to see if a fast-jet pilot, flying a Tornado perhaps, could control a pack of four UAVs in deep, target attack situations while still doing his own job."
To find out, Qinetiq fitted a system called the UAV Command and Control Interface (UAVCCI), to an ageing BAC 1-11 – a 1960s era 100-seat twin-engine jetliner, made by the British Aircraft Corporation.
Under civil aviation law, the pilot controlling the jetliner still had to be on board the aircraft. But he sat at the back of the plane using only the UAVCCI to control the large jet, along with four computer-simulated UAVs on a virtual attack mission.
The UAVCCI uses software agents to control each aircraft under its command, minimising the pilot's workload. This makes each of the UAVs semi-autonomous: they fly straight and level on their own and can be given simple orders using a point-and-click interface on what Williams calls "a simple, flat, moving map".
"The pilot only had to give top level instructions to the UAVs on where to go and what weapons to use, not fly them minute-by-minute," says Ben White, a Qinetiq spokesman.
[...]
Next March, the UAVCCI will face a much harder test. From the cockpit of a Tornado fighter, the pilot will have to fly the Tornado, the unpiloted BAC1-11 and several simulated UAVs.
Controlling multiple uncrewed vehicles and ground robots is a major aim of NATO defence researchers and the US Pentagon wants one-third of its military "assets" to be robotic or remotely controllable by 2015.
Polonium 210 - Easily Obtained in the US via the Internet
The radioactive material that killed a former Russian spy in Britain can be bought on the Internet for $69.
Polonium-210, which experts say is many times more deadly than cyanide, can be bought legally through United Nuclear Scientific Supplies, a mail-order company that sells through the Web, based in Sandia Park, N.M. Chemcial companies sell the Polonium-210 legally for industrial use, such as removing static electricity from machinery. United Nuclear claims that it's "currently the only legal Alpha source available without a license."
The type of Polonium-210 sold emits alpha radiation, which can't penetrate the skin, but is deadly if swallowed, depending on the amount ingested. The Polonium available on United Nuclear's site can be purchased without a license because the level of radioactivity, 0.1 microcurie, does not pose a danger, a spokesman for the U.S. Nuclear Regulatory Commission said.
"At that level, it's exempt from licenses," NRC spokesman David McIntyre said. "At any exempt quantity, it's not considered a health hazard."
I love this part - "To ensure the longest half-life possible, we do NOT keep isotopes in stock. All isotopes are produced fresh in a Nuclear Reactor and shipped directly to you from the NRC licensed isotope manufacturer."
HackReport: Interview with Lance Spitzner, Founder of the Honeynet Project
In my mind, Lance is right on the money when he said the following:
"Even with better technology, better OS security, stronger passwords, better policies it just makes it more difficult and time consuming for the bad guys but they can spend all the time since there is no fear of prosecution. So much profit for so little risk. Hacking is just a tool for extortion, fraud, identity theft, things that have been happening for a long time. If we want to make it more difficult for them we have to bump up the risk as a deterrence."
IRC Bot Attacks Symantec Overflow from May 2006
Via Arbor Networks -
Back in May of this year, Symantec released an avisory entitled SYM06-010: Symantec Client Security and Symantec AntiVirus Elevation of Privilege. Those that took the time to read it beyond the title noticed that this isn’t just a local privilege elevation exploit. It’s an out and out remote stack overflow using a specific service (TCP port 2967). We started tracking possible exploit activity for this vulnerability in early June using an ATF policy to detect scans and exploit, with our thinking that someone would surely take an interest. Activity for this policy quickly dropped off our radar, buried underneath some juicy Windows and VNC holes that people focused on. We didn’t see many scanners for this service, and only a burst of a scan early last week.
That is, until now, in late November, when we see a bot using an exploit for this (and lots of people are curious). We had a look at the bot, and found that it’s a new exploit plugin for a garden variety SDBot. This thing’s a beast! It’s huge, not unlike a bloated bot that someone’s thrown everything into. A partial list of the capabilities this puppy appears to have:
- SYMC06-010 exploit (TCP port 2967)
- NetAPI (MS06-040), TCP port 445
- DDoS and packet flooding (SYN, ACK, ICMP, UDP floods, for example)
- Password theft and packet sniffing
- It can enumerate other installed malware
- The usual bunch of access capabilities
- The usual bunch of brute force attacks, downloads, upload, proxy checks, etc
Thirteen Great Mysteries of Science
Via NewScientist.com -
- The Placebo Effect - Don't try this at home. Several times a day, for several days, you induce pain in someone. You control the pain with morphine until the final day of the experiment, when you replace the morphine with saline solution. Guess what? The saline takes the pain away.
- The Horizon Problem - Our universe appears to be unfathomably uniform. Look across space from one edge of the visible universe to the other, and you'll see that the microwave background radiation filling the cosmos is at the same temperature everywhere. That may not seem surprising until you consider that the two edges are nearly 28 billion light years apart and our universe is only 14 billion years old. Nothing can travel faster than the speed of light, so there is no way heat radiation could have travelled between the two horizons to even out the hot and cold spots created in the big bang and leave the thermal equilibrium we see now.
- Ultra-Energetic Cosmic Rays - For more than a decade, physicists in Japan have been seeing cosmic rays that should not exist. Cosmic rays are particles - mostly protons but sometimes heavy atomic nuclei - that travel through the universe at close to the speed of light. Some cosmic rays detected on Earth are produced in violent events such as supernovae, but we still don't know the origins of the highest-energy particles, which are the most energetic particles ever seen in nature. But that's not the real mystery.
- Belfast Homeopathy Results - Madeleine Ennis, a pharmacologist at Queen's University, Belfast, was the scourge of homeopathy. She railed against its claims that a chemical remedy could be diluted to the point where a sample was unlikely to contain a single molecule of anything but water, and yet still have a healing effect. Until, that is, she set out to prove once and for all that homeopathy was bunkum. In her most recent paper, Ennis describes how her team looked at the effects of ultra-dilute solutions of histamine on human white blood cells involved in inflammation. These "basophils" release histamine when the cells are under attack. Once released, the histamine stops them releasing any more. The study, replicated in four different labs, found that homeopathic solutions - so dilute that they probably didn't contain a single histamine molecule - worked just like histamine. Ennis might not be happy with the homeopaths' claims, but she admits that an effect cannot be ruled out.
- Dark Matter - Take our best understanding of gravity, apply it to the way galaxies spin, and you'll quickly see the problem: the galaxies should be falling apart. Galactic matter orbits around a central point because its mutual gravitational attraction creates centripetal forces. But there is not enough mass in the galaxies to produce the observed spin.
- Viking's Mars Methane - July 20, 1976. Gilbert Levin is on the edge of his seat. Millions of kilometres away on Mars, the Viking landers have scooped up some soil and mixed it with carbon-14-labelled nutrients. The mission's scientists have all agreed that if Levin's instruments on board the landers detect emissions of carbon-14-containing methane from the soil, then there must be life on Mars. Viking reports a positive result. Something is ingesting the nutrients, metabolising them, and then belching out gas laced with carbon-14.
- Tetraneutrons - Four years ago, a particle accelerator in France detected six particles that should not exist. They are called tetraneutrons: four neutrons that are bound together in a way that defies the laws of physics. Francisco Miguel Marquès and colleagues at the Ganil accelerator in Caen are now gearing up to do it again. If they succeed, these clusters may oblige us to rethink the forces that hold atomic nuclei together.
- The Pioneer Anomaly - This is a tale of two spacecraft. Pioneer 10 was launched in 1972; Pioneer 11 a year later. By now both craft should be drifting off into deep space with no one watching. However, their trajectories have proved far too fascinating to ignore. That's because something has been pulling - or pushing - on them, causing them to speed up.
- Dark energy - It is one of the most famous, and most embarrassing, problems in physics. In 1998, astronomers discovered that the universe is expanding at ever faster speeds. It's an effect still searching for a cause - until then, everyone thought the universe's expansion was slowing down after the big bang.
- The Kuiper Cliff - If you travel out to the far edge of the solar system, into the frigid wastes beyond Pluto, you'll see something strange. Suddenly, after passing through the Kuiper belt, a region of space teeming with icy rocks, there's nothing.
- The Wow Signal - It was 37 seconds long and came from outer space. On 15 August 1977 it caused astronomer Jerry Ehman, then of Ohio State University in Columbus, to scrawl "Wow!" on the printout from Big Ear, Ohio State's radio telescope in Delaware. And 28 years later no one knows what created the signal. "I am still waiting for a definitive explanation that makes sense," Ehman says.
- Not-so-Constant Constants - In 1997 astronomer John Webb and his team at the University of New South Wales in Sydney analysed the light reaching Earth from distant quasars. On its 12-billion-year journey, the light had passed through interstellar clouds of metals such as iron, nickel and chromium, and the researchers found these atoms had absorbed some of the photons of quasar light - but not the ones they were expecting.
- Cold Fusion - After 16 years, it's back. In fact, cold fusion never really went away. Over a 10-year period from 1989, US navy labs ran more than 200 experiments to investigate whether nuclear reactions generating more energy than they consume - supposedly only possible inside stars - can occur at room temperature. Numerous researchers have since pronounced themselves believers.
Gingrich Says Govt May Have to Limit Free Speech in the Name of Terror
Former House Speaker Newt Gingrich used a New Hampshire event dedicated to freedom of speech to say the United States will have to re-examine that constitutional right as it fights terrorism.
Speaking in Manchester Monday night, Gingrich said the country may need a different set of rules to reduce terrorists' ability to use the Internet and free speech to recruit and get out their message.
The former speaker also said he won't decide whether to run for president until September 2007.
He spoke at the annual Nackey S. Loeb First Amendment award dinner.
Monday, November 27, 2006
(IN)SECURE Magazine - Issue 1.9 Released
This issue includes:
- Effectiveness of security by admonition: a case study of security warnings in a web browser setting
- Interview with Kurt Sauer, CSO at Skype
- Web 2.0 defense with AJAX fingerprinting and filtering
- Hack In The Box Security Conference 2006
- Where iSCSI fits in enterprise storage networking
- Recovering user passwords from cached domain records
- Do portable storage solutions compromise business security?
- Enterprise data security - a case study
- Creating business through virtual trust: how to gain and sustain a competitive advantage using information security
Russian FSB - Friend or Foe?
What is Russia’s real role in the efforts to combat terrorism? While the Bush administration seems to cling to the notion that Russia is an ally, there are several developments that point in the opposite direction.
The first, of course, is the assassination of Alexander Litvinenko, where the foul play of the Russian security apparatus, closely tied to Mr. Putin, is the prime suspect. The fact that the murder was committed in London and dismissed out of hand as unimportant by Mr. Putin show both a new boldness and the lack of any pretense of accountability by the Russians.
There is also the arming of Iran and help with the Iranian nuclear program, and the close intelligence ties to Hezbollah.
But there is another, barely noticed development in the United States that should be extremely worrisome. A small sporting goods store in rural Pennsylvania was just busted for selling telescopic rifle scopes, binoculars and optics, which need State Department export authorization, to a Russian company that did not have such a license.
As the my colleauge and co-author Stephen Braun write in the Los Angeles Times, the affidavit for carrying out the search states that the Russian company is “Tactica Ltd., a Moscow firm that was described by investigators as ‘a member of the ‘Vympel Group,’ which is a known identifier for an elite counter-terrorism unit that is controlled by the Russian Federal Security Service [formerly the KGB].’”
So, we have Russian intelligence agents illegally buying restricted items in the United States. But it gets better.
A good chunk of the money for the purchases, according to federal officials, came from (hold on Bout fans) Rockman Ltd, a Bulgarian firm owned by Sergei Bout, who has often run Bout companies involved in weapons transactions. As one U.S official told the Times, “Sergei and Viktor’s companies are all under the same umbrella.”
The rest of the money came from Haji Ibrahim, a Pakistani man wanted on federal charges of heroin trafficking. Nice bunch!
The truth is even worse...this happens all the time! We do it to Russia, they do it to us...everyone does it to everyone when possible. Our technology does make us a very very ripe target for this type of activity however.
Big Brother - What Big Ears You Have!
POLICE and councils are considering monitoring conversations in the street using high-powered microphones attached to CCTV cameras, write Steven Swinford and Nicola Smith.
The microphones can detect conversations 100 yards away and record aggressive exchanges before they become violent.
The devices are used at 300 sites in Holland and police, councils and transport officials in London have shown an interest in installing them before the 2012 Olympics.
The interest in the equipment comes amid growing concern that Britain is becoming a “surveillance society”. It was recently highlighted that there are more than 4.2m CCTV cameras, with the average person being filmed more than 300 times a day. The addition of microphones would take surveillance into uncharted territory.
The Association of Chief Police Officers has warned that a full public debate over the microphones’ impact on privacy will be needed before they can be introduced.
The equipment can pick up aggressive tones on the basis of 12 factors, including decibel level, pitch and the speed at which words are spoken. Background noise is filtered out, enabling the camera to focus on specific conversations in public places.
UK Police Create Criminal Profile Database for 'Future' Suspects
Criminal profilers are drawing up a list of the 100 most dangerous murderers and rapists of the future even before they commit such crimes, The Times has learnt.
The highly controversial database will be used by police and other agencies to target suspects before they can carry out a serious offence. Pilot projects to identify the highest-risk future offenders have been operating in five London boroughs for the past two months.
The Soham murderer Ian Huntley and the serial rapist Richard Baker have been used as examples of the type of man police will identify.
However, the database will increase concerns at the growth of official surveillance and anxieties that innocent men are being singled out for offences they have no intention of committing.
Experts from the Metropolitan Police’s Homicide Prevention Unit are creating psychological profiles of likely offenders to predict patterns of criminal behaviour. Statements from former partners, information from mental health workers and details of past complaints are being combined to identify the men considered most likely to commit serious violent crimes.
The list will draw comparisons with the Hollywood film Minority Report, in which suspects are locked up before they can commit a predicted crime.
Laura Richards, a senior criminal psychologist with the Homicide Prevention Unit, told The Times: “My vision is that we know across London who the top 100 people are. We need to know who we are targeting.
“It is trying to pick up Ian Huntley before he goes out and commits that murder. Then we have the opportunity to stop something turning into a lethal event.”
The team is concentrating on reducing the risk of those with a history of domestic violence turning into murderers. About a quarter of murders are related to domestic violence.
“There are some pretty dangerous people out there, so you need these risk models to wheedle them out, separate the wheat from the chaff,” she said. “If you add up all the information, it tells us which people are risky.”
Ms Richards said that once an individual had been identified, police would decide whether to make moves towards an arrest, or to alert the relevant social services who could steer those targeted into “management programmes.”
The project will be closely watched by the Home Office. However, civil liberties groups and human rights lawyers will be concerned at the plans to intervene in the lives of men before they actually commit a crime.
Details of the database emerged after Richard Thomas, the Information Commissioner, said that Britain had “sleepwalked” into a surveillance society.
Simon Davies, director of Privacy International, said yesterday: “It is quite right that the police should keep intelligence on suspected criminals, but it is obscene to suggest there should be a ‘crime idol’ list of those who might commit an offence.
“The police are systematically moving the boundaries as to where they can exercise their powers. The Minority Report syndrome is pushing the boundary of criminal intervention further into the general community.”
There was also concern that the database would be ineffective if the authorities continued to fail to act on the information already available to them. Ray Wyre, a sexual crimes consultant, was supportive of the database but said that it would only work if police acted on the information.
“Of course you have to know your enemy, but it is what you do with the data that matters,” he said.
The United Kingdom is proudly leading the push into the "Brave New World". Perhaps I should just take my daily dose of Soma and be quiet.....
Sunday, November 26, 2006
Video Game Makers are Worse than Dope Dealers
These video game manufacturers ought to be taken out back and fed to the virtual hogs.
Last Sunday, my daughter, Rachel, 15, asked if we could go to Best Buy so she could check out a video game she loves called "Zelda."
"I just want to hold it," she said.
That sounded to me like a plea from a kid who really wants to own this game. So I suggested to my wife, Kay, and Rachel that we go to the store and just buy "Zelda."
Not that I understand the frenzy here. I'm so low-tech I can limbo under a gigabyte. I don't know "Zelda" from "Alice in Wonderland."
But I figure if a kid wants a $50 game bad enough to just "hold it," I could spring for that.
That's when I was told the game needed a $250 game system, something mysterious called a Wii.
Undaunted, I figured, what the heck, let's go for it. To make a kid happy, I can get out the checkbook.
So on Sunday afternoon, the three of us headed off to the store to buy "Zelda" and Wii, or so I thought.
We hit about half a dozen South Austin stores and couldn't find either the game or the system.
Seems like the miserable creeps at Nintendo, the video company that makes both the game and the system, had sent out just enough Wiis to create what is known as market interest.
When we left the house, Rachel was bubbly and happy. Heck, she even voluntarily cleaned her room, the biggest upset I'd seen since the Red Sox won the World Series.
But by the time we found out the Target on Ben White Boulevard had run out of Wiis, Rachel was in tears. I felt like a bag of ham.
They were out at Best Buy, too. The clerk told us that there was a guy lurking about the floor, offering to sell his Wii for $450 to distraught customers who couldn't find one. He suggested we track him down.
This attempt by the toy manufacturers to turn our children into emotional wrecks began in the '80s with the Cabbage Patch doll.
My idea of Cabbage Patch Doll aerobics would be to drag one behind a truck.
But American grandmothers didn't see it that way. Oh, no, the old birds loved this doll because their grandkids wanted one.
So the long gray line would form outside the store at 6 a.m. Then, when the doors sprung open at 7, these old women would beat each other over the head with their handbags to get their wrinkled fingers on a doll.
This tradition of rioting over polyurethane products continues today with video games. Last week, a man was shot while standing in line for a Sony PlayStation 3.
Sony ought to make an action game out of that: a bunch of cartoon shoppers in line waiting to buy toys while the bad guy on the screen guns them down for points.
Why can't you greedy buzzards at the game companies send out enough of your product to start with so we don't all go crazy? Or is that just too much to ask?
Well said...whats up with that?
Saturday, November 25, 2006
Tools of the Trade - Now with Beta-Carotene!
New features:
- Cain's MitM NTLM Challenge Spoofing. (Requires APR to be active and a MitM condition between victim hosts).You can now spoof server challenges in NTLM authentications; this feature enables the use of RainbowTables for cracking network hashes. WARNING !!! Enabling Challenge Spoofing cause users to fail authentications so use it carefully.
- NTLM Session Security authentications downgrade to LM&NTLMv1. The following protocols are supported: SMB, DCE/RPC, TDS, HTTP, POP3, IMAP, SMTP.
- LM + spoofed challenge Hashes Cryptanalysis via Sorted Rainbow Tables.
- HALFLM + spoofed challenge Hashes Cryptanalysis via Sorted Rainbow Tables.
- NTLM + spoofed challenge Hashes Cryptanalysis via Sorted Rainbow Tables.
- New types of RainbowTables have been added to Winrtgen v2.2. "lmchall" and "ntlmchall" tables can be used against LM and NTLM response hashes for spoofed challenges (0x1122334455667788). "halflmchall" tables can be used against the first 8 bytes LM response hashes for spoofed challenges to recover the first 7 characters of the original password.
2) Winamp 5.32 has been released. This release does not appear to be in response to any security issues however.
Teenager Builds Nuclear Fusion Reactor in Basement
An American teenager has built a working nuclear fusion reactor in the basement of his parents' home.
Thiago Olson, 17, spent over 1,000 hours and two years getting the reactor to work, scavenging old equipment, buying components on eBay and persuading manufacturers to give him large discounts.
The reactor works by sucking the air from a reaction chamber and injecting in deuterium, a form of hydrogen. A charge of 40,000 volts is then applied, using equipment from a gutted mammogram scanner, forming a small ball of plasma.
"Originally, he wanted to build a hyperbolic chamber," Olson's mother Natalice told the Detroit Free Press, adding that she promptly said "no". But, when he asked about the nuclear fusion machine, she relented.
"I think it was pretty brave that he could think that he was capable to do something so amazing," she said.
The process itself is safe since the reaction ends as the power drops. It emits very low levels of X-rays which are not at harmful levels.
Olson, who is nicknamed 'Mad Scientist' by his friends, intends to pursue a career in physics research.
"I thought he was going to be a cook, because he liked to mix things," said Natalice Olson.
Friday, November 24, 2006
Mujahideen in Lebanon Allege Hezbollah and Syrian Intelligence Assassination Plot
In a message posted to a password-protected forum today, Tuesday, November 21, 2006, the Mujahideen in Lebanon responded to the assassination of Minister Pierre Amin Gemayel in Beirut, an event which occurred only hours earlier. The group claims that Hezbollah, in coordination with Syrian intelligence, is directly responsible for the assassination, and further, that an effort is under way to frame the incident as an al-Qaeda operation.
The statement reads: “The assassination was directly executed by five individuals from Hezbollah. They were divided into two cars and a yellow motorcycle.” The group alleges a false statement was printed prior to the assassination, in the refugee camp Nahr al-Bared, in which al-Qaeda is implicated in the attack. The Mujahideen in Lebanon view the assassination of Minister Gemayel as part of a continued effort on the part of Hezbollah and its Syrian backers to coerce Shia ministers into withdrawal, ultimately facilitating an overthrow of the Lebanese government.
The statement closes, “We are monitoring them,” referring to Syrian-supported Shi’ites in Lebanon.
Radioactive Polonium-210 Found in Blood of Russian Ex-Spy
Traces of radioactive polonium have been found in the blood of the deceased Russian ex-spy Alexander Litvinenko, the UK’s Health Protection Agency (HPA) said on Friday. His urine also tested positive for radiation.
“This is an unprecedented event in the UK,” said HPA chief executive Pat Troop. “It is the first time someone in the UK has apparently been deliberately poisoned with a radioactive agent.”
The agency is now assessing the health risks posed to members of the public who may have come into contact with Litvinenko, including family members and hospital staff who cared for him during the weeks he spent in hospital. They are also trying to decide the safest way for pathologists to conduct an autopsy of his body, and indeed whether such a procedure is safe enough to be performed at all.
Litvinenko, aged 43, died on Thursday of heart failure after claiming he had been poisoned in a London restaurant. He was formerly an agent of the Soviet, then the Russian, security service. He specialised in investigating organised crime and its involvement with corrupt officials.
High levels of radiation have been discovered in a central London hotel that Litvinenko frequented, and at the sushi restaurant where he said he ate on 1 November 2006. The restaurant has now been closed, said the HPA.
“Tests have established that Mr Litvinenko had a significant quantity of the radioactive isotope polonium-210 in his body,” the HPA announced on Friday. “It is not yet clear how this entered his body. Police are investigating this.”
[...]
"To poison someone, large amounts of polonium-210 are required and this would have to be manmade, perhaps from a particle accelerator or a nuclear reactor," said Dudley Goodhead at the UK's MRC Radiation and Genome Stability Unit. “Polonium has a half-life of 138 days. This means that if that was the poison it will still be in the body and in the area – which makes it relatively easy to identify.”
China Obtains B-2 Stealth Engine Secrets
China obtained secret stealth technology used on B-2 bomber engines from a Hawaii-based spy ring in a compromise U.S. officials say will allow Beijing to copy or counter a key weapon in the Pentagon's new strategy against China.
Details of the classified defense technology related to the B-2's engine exhaust system and its ability to avoid detection by infrared sensors were sold to Chinese officials by former defense contractor Noshir S. Gowadia, an Indian-born citizen charged with spying in a federal indictment released by prosecutors in Hawaii.
Additionally, Mr. Gowadia provided extensive technical assistance to Chinese weapons designers in developing a cruise missile with an engine exhaust system that is hard to detect by radar, according to court papers made public recently.
He also helped the Chinese modify a cruise missile so that it can intercept U.S. air-to-air missiles, and helped Chinese weapons designers improve testing and measurement facilities, the court papers state.
Most of the indictment, handed up Nov. 8, outlines how the engineer helped China develop a radar-evading stealth exhaust nozzle for a cruise missile engine.
Additionally, the court papers indicated that Mr. Gowadia sent e-mails to Israel, Germany, and Switzerland in 2002 and 2004 that contained data labeled "secret" and "top secret" that was related to U.S. stealth technology intended for use in the TH-98 Eurocopter and for foreign commercial aircraft.
One computer file found in Mr. Gowadia's Maui, Hawaii, home was a file containing the radar cross-sections of U.S. B-1 and F-15 jets and the Air Force's air-launched cruise missile, information that would be useful to countering those systems by anti-aircraft missiles or other air defense weapons.
The case is the second major military technology espionage case involving China. Earlier this year, two Chinese-born brothers in Los Angeles were arrested as suspects in passing Navy warship and submarine weapons secrets to China.
In all, Mr. Gowadia is charged with making at least six secret visits to China from 2002 through 2005, and being paid at least $110,000 by Chinese officials for highly classified defense technology supplied through January, according to court papers. Investigators think he was paid as much as $2 million, some of which remains in foreign bank accounts.
Thursday, November 23, 2006
Urban Word of the Day - Tryptophanatic
One who eats until they are engorged...and then proceeds to eat even more, usually resulting in a turkey coma. A glutton -- but a happy glutton nontheless.See also Thanksgiving and Grandma's cooking.
"Yeah, I was a total tryptophanatic over the holidays. I think I slept for about 30 hours after I ate that second turkey."
Tuesday, November 21, 2006
Tools of the Trade - 2 Grams of Fiber per Serving!
- Fixed (I hope) a bug related to Pcap capture on Mac OS X. Thanks to Christophe Thil for reporting the problem and to Kurt Grutzmacher and Diman Todorov for helping to track it down.
- Integrated all of your OS detection submissions since ALPHA11. The DB has increased 27% to 189 signatures. Notable additions include the Apple Airport Express, Windows Vista RC1, OpenBSD 4.0, a Sony TiVo device, and tons of broadband routers, printers, switches, and Linux kernels. Keep those submissions coming!
- Upgraded the included LibPCRE from version 6.4 to 6.7. Thanks to Jochen Voß (voss(a)seehuhn.de) for the suggestion (he found some bugs in 6.4)
2) On Nov 16th, Snort 2.6.1 was released. Snort 2.6.1 provides new functionality including the following:
- New pattern matcher with a significantly reduced memory footprint
- Introduction of stream5 for experimental use
- Improvements to stream4, including UDP session tracking and optimizations for the reassembly buffer
- Handling for reassembly of SMB fragmented data in DCE/RPC
- An ssh preprocessor for experimental use
- Updated Snort decoder that can decode GRE encapsulated packets
- Output plugin to allow Snort to configure Aruba access control
- Bug fixes and performance improvements
Pitch Black Metal Created with a Laser Pulse
"We've been surprised by the number of possible applications for this," says Chunlei Guo, assistant professor of optics at the University of Rochester." We wanted to see what would happen to a metal's properties under different laser conditions and we stumbled on this way to completely alter the reflective properties of metals."
The key to creating black metal is an ultra-brief, ultra-intense beam of light called a femtosecond laser pulse. The laser burst lasts only a few quadrillionths of a second. To get a grasp of that kind of speed--a femtosecond is to a second what a second is to about 32 million years.
During its brief burst, Guo's laser unleashes as much power as the entire grid of North America onto a spot the size of a needle point. That intense blast forces the surface of the metal to form and nanostructures--pits, globules, and strands that both dramatically increase the area of the surface and capture radiation. Some larger structures also form in subsequent blasts.
Guo's research team has tested the absorption capabilities for the black metal and confirmed that it can absorb virtually all the light that fall on it, making it pitch black.
This trick increases the exposed surface area of the metal exponentionally, very cool stuff indeed.
Five Reasons To Ignore John Gruber’s OS X Security Pundity
Today’s Daring Fireball post has two objectives:
- To tar eWeek Security pundit Larry Setzer, and the trade press in general, as biased, lazy, and incompetent when it comes to Mac security.
- To claim that Mac security is better than Windows security.
We can get behind one of those objectives. But Gruber isn’t going to let us do that: instead, he borrows support for his defensible argument to shore up a weak argument. This isn’t a new idea; it’s straight out of the Mac zealot playbook, and it’s the same tactic Gruber used during the Mac wireless debacle when he hid behind Brian Krebs’ reporting to throw a smoke screen over OS X kernel wireless vulnerabilities.
Here’s an example from today’s article. <;/em>Seltzer’s article claims that a recently released Symantec report on OS X security “revealed a collection of vulnerabilities and potential attacks that rivaled any major operating system”, and “in fact things are getting worse.” Instead of arguing that Seltzer doesn’t (and can’t) support that argument with facts, which would be boring, Gruber plays to his base: “nowhere in the report does it indicate that the ‘collection’ as a whole rivals that of any other operating system.”
But that’s an equally indefensible argument! Seltzer himself names operating systems that are in positions comparable to OS X: Linux and Solaris. Gruber’s M.O. is simple and he counts on his audience not to notice it: when a pundit or reporter overreaches, Daring Fireball leaps on the opportunity to claim that the opposite argument is true. It almost never is.
Please read the full blog from the link at the top. Thomas is spot on. I couldn't say it better myself. I saw the OSX blog entry this morning and was thinking the same thing. Of course, John totally overlooks the Metasploit OS X wireless vulnerability that was released recently....and if he thinks the "shipping" version isn't open to the same type of attack...he is sorely mistaken.
Just because Apple doesn't like to talk about their holes doesn't mean that people are exploiting them already...John must remember that a blackhat world does exist and they have exploits that will never be released. How quickly we forget about the OS X kernel flaw that was released during MoKB (which BSD patched years ago)...
Week of Oracle Database Bugs (WoODB)
The Week of Oracle Database Bugs
Based on the great idea of H D Moore "Month of Browser Bugs" and LMH "Month of Kernel Bugs", we are proud to announce that we are starting on December the "Week of Oracle Database Bugs" (WoODB).
What is the WoODB about?
An Oracle Database 0day will be released every day for a week on December.
Why are you doing this?
We want to show the current state of Oracle software ("in")security also we want to demostrate Oracle isn't getting any better at securing its products (you already know the history: two years or more to fix a bug, not fixing bugs, failing to fix bugs, lying about security efforts, etc, etc, etc.).
Why are you targeting only Oracle?
We have 0days for all Database software vendors but Oracle is "The #1 Star" when talking about lots of unpatched vulnerabilities and not caring about security.
Why not the Month of Oracle Database Bugs?
We could do the Year of Oracle Database Bugs but we think a week is enough to show how flawed Oracle software is, also we don't want to give away all our 0days:), anyways if you want to contribute send your Oracle 0days so this can be extended for another week or more.
Symantec : Me code write good - The l33t skillz of the virus writer
http://www.symantec.com/avcenter/reference/me.code.write.good.pdf
It deals with the buggy code that can commonly be found in worms / viruses.
It is an interesting read, but I was sad to see one big virus bug missing.
The Sasser FTPD Exploit. The exploit attacked a buffer overflow in the FTPD server installed and used by almost all major variants of the Sasser worm.
I remember when that exploit was released and it was just too funny...an exploit created for a vulnerability in a virus that was designed to target another operating system vulnerability.
Irony is funny sometimes...
'Beer Goggles' Research Commissioned by Bausch & Lomb
The drink-fuelled phenomenon is said to transform supposedly "ugly" people into beauties - until the morning after.
Researchers at Manchester University say while beauty is in the eye of the beer-holder, the amount of alcohol consumed is not the only factor.
Additional factors include the level of light in the pub or club, the drinker's own eyesight and the room's smokiness.
The distance between two people is also a factor.
They all add up to make the aesthetically-challenged more attractive, according to the formula.
The formula can work out a final score, ranging from less than one - where there is no beer goggle effect - to more than 100.
Nathan Efron, Professor of Clinical Optometry at the University of Manchester, said: "The beer goggles effect isn't solely dependent on how much alcohol a person consumes, there are other influencing factors at play too.
"For example, someone with normal vision, who has consumed five pints of beer and views a person 1.5 metres away in a fairly smoky and poorly lit room, will score 55, which means they would suffer from a moderate beer goggle effect."
The research was commissioned by eyecare firm Bausch & Lomb PureVision.
A poll showed that 68% of people had regretted giving their phone number to someone to whom they later realised they were not attracted.
A formula rating of less than one means no effect. Between one and 50 the person you would normally find unattractive appears less "visually offensive".
Non-appealing people become suddenly attractive between 51 and 100. At more than 100, someone not considered attractive looks like a super model.
See the link above for the formula...good stuff.
Man Arrested with $78,000 and Data about Nukes & Cyanide
DETROIT - A man was arrested at Detroit Metropolitan Airport after officials say they found him carrying more than $78,000 in cash and a laptop computer containing information about nuclear materials and cyanide.
Sisayehiticha Dinssa, an unemployed U.S. citizen, was arrested Tuesday after a dog caught the scent of narcotics on cash he was carrying, according to an affidavit filed in court.
When agents asked him if he had any cash to declare, he said he had $18,000, authorities said. But when agents checked his luggage, they found an additional $59,000. When they scrolled through his laptop, they said they found the mysterious files.
At a court hearing Wednesday, Dinssa was ordered held in custody until at least until Monday at the request of prosecutors.
Assistant U.S. Attorney Leonid Feller argued Dinssa was a potential risk to the community and federal agents want to get a warrant to search his computer more thoroughly, The Detroit News reported Thursday. U.S. Magistrate Donald Scheer approved Feller’s request to detain him.
Dinssa, who is from Dallas, arrived in Detroit from Nigeria by way of Amsterdam and was headed for Phoenix, Feller said. He is charged with concealing more than $10,000 in his luggage, which carries a maximum penalty of five years in prison, the Detroit Free Press reported.
A message seeking comment was left Thursday with his lawyer, Leroy Soles.
I always love these vauge news reports of people having "information about nuclear materials"...what does that mean? I wouldn't call him a terrorist, but he was clearly doing something he shouldn't be doing...
Who would go to Phoenix from Nigeria via Amsterdam and Detroit?...it isn't like he didn't have the money to get a more direct flight. Very fishy indeed...
So we found this guy, what about the other 10 that grabbed their bags before the dog was around?
Humor: Making Critical Decisions
"Deciding Like A Ninja"
Monday, November 20, 2006
Social Networks and the Importance of “Who You Know”
The old bromide is truer than ever. It’s not what you know, it’s who you know. And it’s especially who knows you. The emergence and influence of a whole new breed of social networks is a rapidly growing phenomenon. Moreover, a number of people are paying attention to social networks — not just anthropologists, but historians, business leaders, and a host of teenagers.
In large part, we can thank — or blame — the Internet. Despite its vast size and complexity, the Internet has turned out to be a profoundly personal venue. People around the globe are forming connections based on every conceivable common interest, from the serious and practical to the outright silly. In 2005, the 80-million-member networking Web site MySpace, a gathering place where people introduce themselves publicly to friends and strangers, received more page views than Google. And the movement continues to grow.
[...]
Mr. Gladwell identifies three types of social networkers: Mavens, Connectors, and Salesmen. Mavens love to gather knowledge and pass it on to others: Mr. Gladwell describes one Maven who didn’t just recommend a Volvo to a colleague, he accompanied him when he went to buy one to ensure he got the best deal. The Maven likes to exercise expertise and be helpful.
Connectors seem to know everyone. They can get information where it needs to go because they just love to connect. Paul Revere, best known for rallying Middlesex, Mass., farmers with his cry, “The British are coming!” in the Revolutionary War, was a classic Connector, with a knack for knowing and attracting people. Had the silversmith been less gregarious, argues Mr. Gladwell, then the colonists might have lost.
Salesmen can be great persuaders. They are irresistibly positive; their ideas and attitudes are infectious. In effect, their positive emotions transmit to other people. Mr. Gladwell gives the example of Tom Gau, a financial planner in southern California, who made a ridiculously low bid on a new home, yet persuaded the seller to accept it. When these three types of people interact in the context of a social network, little ideas can turn into big deals with astonishing speed.
I am currently working as a pen-tester for an international financial institution in Austin TX. I didn't learn about this job from Monster.com or from the paper....a friend in the UK told me about the opening. I passed my resume to him and he sent it back to TX...which got me the interview.
I met this friend 2-3 years old again while on the Full Disclosure security mailing list...and we have never met in real life. I have only spoken with him on the phone once....
So if anyone can tell you how true the above story is...it is me.
Israel Attempts to Take UAVs to the Nano-Scale
JERUSALEM (Reuters) - Israel is using nanotechnology to try to create a robot no bigger than a hornet that would be able to chase, photograph and kill its targets, an Israeli newspaper reported on Friday.
The flying robot, nicknamed the "bionic hornet", would be able to navigate its way down narrow alleyways to target otherwise unreachable enemies such as rocket launchers, the daily Yedioth Ahronoth said.
It is one of several weapons being developed by scientists to combat militants, it said. Others include super gloves that would give the user the strength of a "bionic man" and miniature sensors to detect suicide bombers.
The research integrates nanotechnology into Israel's security department and will find creative solutions to problems the army has been unable to address, Deputy Prime Minister Shimon Peres told Yedioth Ahronoth.
"The war in Lebanon proved that we need smaller weaponry. It's illogical to send a plane worth $100 million against a suicidal terrorist. So we are building futuristic weapons," Peres said.
The 34-day war in Lebanon ended with a U.N.-brokered ceasefire in mid-August. The war killed more than 1,200 Lebanese, mostly civilians, and 157 Israelis, mostly soldiers.
Prototypes for the new weapons are expected within three years, he said.
'Second Life' hit by Worm - Players Blindly Help
A self-replicating worm Linden Lab dubbed "grey goo" overtook online world Second Life Sunday, forcing the world's owners to block all logins but their own for about half an hour. According to comments on the company's blog, the worm planted spinning gold rings in the world. Perhaps a Pavlovian response by fans of Sega's old Sonic the Hedgehog game, or an indication of the general curious nature of people playing Second Life, players willingly interacted with the objects, spreading the worm even further. As the worm spread, players reported serious lag in the virtual world.
According to blog entries posted by Linden Lab, the company blocked users from logging in at about 2:45pm PST in order to manually eradicate the virtual world of the rings. Login capabilities were restored half an hour later.
The worm may well be the largest of its kind to hit an online world.
Sunday, November 19, 2006
Attacking RSA with Simple Branch Prediction Analysis (SBPA)
Very recently, a new software side-channel attack, called Branch Prediction Analysis (BPA) attack, has been discovered and also demonstrated to be practically feasible on popular commodity PC platforms. While the above recent attack still had the flavor of a classical timing attack against RSA, where one uses many execution-time measurements under the same key in order to statistically amplify some small but key-dependent timing differences, we dramatically improve upon the former result. We prove that a carefully written spy-process running simultaneously with an RSA-process, is able to collect during one \emph{single} RSA signing execution almost all of the secret key bits. We call such an attack, analyzing the CPU's Branch Predictor states through spying on a single quasi-parallel computation process, a {Simple Branch Prediction Analysis (SBPA)} attack --- sharply differentiating it from those one relying on statistical methods and requiring many computation measurements under the same key. The successful extraction of almost all secret key bits by our SBPA attack against an openSSL RSA implementation proves that the often recommended blinding or so called randomization techniques to protect RSA against side-channel attacks are, in the context of SBPA attacks, totally useless.
Updated UK Computer Misuse Act Damaging to Secuirty Research
The Police and Justice Bill 2006, which received Royal Assent last Wednesday, contains amendments to the Computer Misuse Act 1990 that alter the law surrounding the creation and distribution of 'dual use' software tools. These are tools such as nmap — a security scanner — which are primarily used by legitimate users and security researchers, but can also be used by hackers to scan networks for vulnerabilities.
The amendments to the law could potentially prohibit the downloading of such security tools, according to Malcolm Hutty, head of public affairs at the London Internet Exchange (LINX).
"We do have to have responsible software supply. However, [under these amendments] any form of download tool could be prohibited," said Hutty earlier this week. "The Government is inadvertently throwing the baby out with the bathwater."
Part 37 of the Police and Justice Bill amends section 3A, clause 2 of the CMA, and states: "A person is guilty of an offence if he supplies or offers to supply any article believing that it is likely to be used to commit, or to assist in the commission of, an offence."
This will place serious constraints on the distribution of security tools, as the prosecution must only prove that the distributor believed it was likely that the tool will be used for hacking, even if this was not his intention, said Richard Clayton, a Cambridge University security expert. This would include malware researchers, ISPs and universities that host download tools, Clayton claimed.
Malware researchers could also be severely constrained by the new law because of the definition of "article", according to Clayton and Hutty. Clause 4 of section 3A states: "In this section 'article' includes any program or data held in electronic form."
The law is supposed to cover virus writing and hacking tools, but the wording of the law also covers the disclosure of software flaws, according to Hutty.
"In theory this covers the announcement of software flaws. The fear in the security world is that the legislation makes it possible for a vendor to come along and say that if security researchers are making [software-flaw] information available to the public, they must know it will be used to exploit software, as well as used for beneficial purposes," said Hutty. "The chilling effects on security research is a concern."
Clayton added: "If you approach a company and say you've found a problem, they can issue a writ to silence you. HSBC threatened to sue the Guardian [over reports of research by Cardiff University into HSBC's online banking authentication procedure]. This shows people are starting to think about going to the law to deal with bad news about security."
Old Web Censorship Law Might Become Enforceable?
Introduced by Rep. Mike Oxley (R-Ohio) in 1999, the Child Online Protection Act (COPA) makes it a crime for commercial Web sites to give minors access to "harmful material," defined as any sexually explicit communication that lacks "serious literary, artistic, political, or scientific value." Violators face up to $50,000 in fines and six months in prison.
This affects far more than just porn producers -- even news organizations publishing articles and videos that could be deemed "harmful to minors" might be in trouble. Just last week, the Florida Supreme Court upheld a state version of COPA that restricted e-mail that could be deemed "harmful to minors."
Shortly after the bill was introducted, The American Civil Liberties Union immediately filed a lawsuit to block the U.S. Justice Department, and a federal judge granted an injunction barring prosecutors from enforcing the law. That injunction has been in place ever since.
But now that could change. On Monday, U.S. District Judge Lowell A. Reed, Jr. in Philadelphia will hear closing arguments in the Child Online Protection Act case, and a ruling is expected by early 2007.
You might remember the big Google vs the Government issue after the government requested huge amount of search terms from all the major search vendors. Well, all of that was for this law...the government had to prove that porn was on the internet. Is it really that hard to prove?
After looking over all the data, the government has deemed 1% of the Internet as Porn. I still think that is very low in my view. They aren't getting P2P, BitTorrent or FTP into account...
Regards, the language used in COPA is much too vague for today's world...
Saturday, November 18, 2006
Friday, November 17, 2006
Cornell Robot Builds its Own "Self-Image"
So Cornell researchers have built a robot that works out its own model of itself and can revise the model to adapt to injury. First, it teaches itself to walk. Then, when damaged, it teaches itself to limp. Although the test robot is a simple four-legged device, the researchers say the underlying algorithm could be used to build more complex robots that can deal with uncertain situations, like space exploration, and may help in understanding human and animal behavior.
The research, reported in the latest issue (Nov. 17) of the journal Science, is by Josh Bongard, a former Cornell postdoctoral researcher now on the faculty at the University of Vermont, Cornell graduate student Viktor Zykov and Hod Lipson, Cornell assistant professor of mechanical and aerospace engineering.
Instead of giving the robot a rigid set of instructions, the researchers let it discover its own nature and work out how to control itself, a process that seems to resemble the way human and animal babies discover and manipulate their bodies. The ability to build this "self-model" is what makes it able to adapt to injury.
"Most robots have a fixed model laboriously designed by human engineers," Lipson explained. "We showed, for the first time, how the model can emerge within the robot. It makes robots adaptive at a new level, because they can be given a task without requiring a model. It opens the door to a new level of machine cognition and sheds light on the age-old question of machine consciousness, which is all about internal models."
The robot, which looks like a four-armed starfish, starts out knowing only what its parts are, not how they are arranged or how to use them to fulfill its prime directive to move forward. To find out, it applies what amounts to the scientific method: theory followed by experiment followed by refined theory.
It begins by building a series of computer models of how its parts might be arranged, at first just putting them together in random arrangements. Then it develops commands it might send to its motors to test the models. A key step, the researchers said, is that it selects the commands most likely to produce different results depending on which model is correct. It executes the commands and revises its models based on the results. It repeats this cycle 15 times, then attempts to move forward.
Playstation 3: What the Hell is Wrong with People?
I am looking over all this Playstation 3 news and I can only wonder -"When did everyone go insane??"
Engadget.com is pulling together a list of PS3 crime cases.
PS3 crime spree, part II: Fall of man
PS3 Line Insanity; Pregnant Woman Tries Not To Give Birth While Waiting
After all it is said and done, your PS3 might be used to break internationally law anyways.
Tools of the Trade - Now with Color Safe Bleach!
1) Just a little note about the Nmap 4.20 Alpha 11. Shortly after installing the alpha, I did a quick test and it didn't seem to work. I had to run, but I told myself to look into the issue later. As it turns out, the alpha install also seem to mess up my fresh Wireshark 0.99.4. ...this only points to one thing - Winpcap.
If you see the follow problem, just uninstall Winpcap and re-install Winpcap 4.0 beta 2 and you should be ok.
C:\Documents and Settings\test\Desktop>nmap 192.168.123.1
Starting Nmap 4.20ALPHA11 ( http://insecure.org ) at 2006-11-17 16:20 Central Standard
Timednet: Failed to open device eth0
QUITTING!
2) Just today, Oxid.it released Cain & Abel v3.9. The Airpcap USB adapter for Windows has been supported since v3.3
Updates for v3.9 listed below:
- Added Ophcrack's RainbowTables support for NTLM Hashes Cryptanalysis attack.
- Added ability to dump MSCACHE hashes directly from SYSTEM & SECURITY registry hive files.
- MSCACHE Hashes Cryptanalysis via Sorted Rainbow Tables.
- ORACLE Hashes Cryptanalysis via Sorted Rainbow Tables.
- New RainbowTable types have been added to Winrtgen v2.0. "mscache" and "oracle" tables can be used against MSCACHE and ORACLE hashes for specific usernames that can be set in the configuration dialog.
3) On Oct. 30th, Tenable Network Security, Inc. announced the availability of Nessus 3.0.4 for Windows, Mac OS X, Linux, Solaris and FreeBSD. The windows port is officially out of beta.
GPS, GSM Cellphone Jammers Hit Mainstream
Don't get too reliant on that GPS receiver, Magellan, since companies are now starting to release devices that locally block GPS signals. Detectnu's device not only block GPS signals within a 50-meter (164-foot) radius, but also GSM cellphone signals in a 20-meter (65-foot) radius. Another such device—the RJ-G1575 GPS jammer from Radixon Hadrian—blocks GPS signals in a 50-kilometer (31-mile) radius. Now, I can completely understand cellphone jammers (hint: people have no concept of tact in New York City and love to yap about God knows what quite loudly), but blocking GPS? What good does that do, other than give mischief makers a rise?
Now if I can just get one of these installed in my car....
The Chewbacca Defense
The term Chewbacca defense is used to refer to any legal strategy or propaganda strategy that seeks to overwhelm its audience or jury with nonsensical arguments, as a way of confusing the audience and drowning out legitimate opposing arguments. It is thus a kind of logical fallacy, specifically, an ignoratio elenchi (red herring) fallacy.
Fear, uncertainty, and doubt (FUD) also can be viewed as a particular case of Chewbacca Defense, where the confusing arguments are tools for the spread of FUD.
The term Chewbacca Defense originated in the animated series South Park. The show satirized attorney Johnnie Cochran's closing argument defending O.J. Simpson in his murder trial.
The term Chewbacca Defense was first used in the South Park episode "Chef Aid", which premiered on October 7, 1998 as the fourteenth episode of the second season.
In the episode, Chef discovers that Alanis Morissette's (fictional) hit song "Stinky Britches" is the same as a song he wrote years ago, before he abandoned his musical aspirations. Chef contacts a "major record company" executive, seeking only to have his name credited as the composer of "Stinky Britches." Chef's claim is substantiated by a twenty-year-old recording of Chef performing the song.
The record company refuses, and furthermore hires Johnnie Cochran, who files a lawsuit against Chef for harassment. In court, Cochran resorts to his "famous" Chewbacca Defense, which he "used during the Simpson trial", according to Gerald Broflovski.
Thursday, November 16, 2006
Tax Dollars at Work: The Air Force Wants to Build "Subterranean Vehicles"
The Air Force wants to build "subterranean vehicles" to attack hard, and deeply buried targets.
See the full SBIR Overview.
SANS Top-20 - 2006 Update
http://www.sans.org/top20/?ref=1814#w1 (PDF)
Thief Uses MP3 Player in Phreaker Style Credit Card Scam
These were then interpreted using a modem line tap, or MLT, acquired from Canada, or passed through a computer software program bought illicitly in Ukraine.
Parsons, of Gorton, Manchester, was able to exploit his knowledge of credit card security systems to put together credit card numbers and the cards’ expiry dates. The gang used the data to encode and clone a number of credit cards.
Wednesday, November 15, 2006
Desktop Background Sites for Geeks

555 Design
Art. Lebedev Studio
Caedes
ClearlyPixelated
DeviantArt
Digital Blasphemy - Top Downloads
Digital Blasphemy - User Gallery
EndEffect.com (wallpapers open in pop-up window)
Flickr Wallpaper Group
GNOME Art
GNOME-Look
Interfacelift
KDE-Look
MacDesktops
Mandolux (stopsign photo above found here)
Pixelgirl
RAILhead Design
Sensitive Light
ShiftedReality
Skeedz
TwistedSun
VladStudio
Tuesday, November 14, 2006
Symantec: The Mac OS X Threat Landscape
Security vendor Symantec has issued a detailed report on current Apple Mac OS X threats, covering a wide range of security issues that affect the platform today.
The 29-page Symantec DeepSight report (PDF) was released on November 13, 2006 and is being made available through SecurityFocus. It offers an in-depth look at the current threat landscape on Mac OS X and is likely the most comprehensive document of its kind for Apple security threats.
The research report looks at significant OS X threats including local, remote and kernel vulnerabilities and then discusses overall system design weaknesses that contribute to insecurities on the Mac platform. The document also reviews the current state of malicious code, discussing the presence of several viruses and worms and the existence of three known rootkits for OS X.
Conclusion - Mac OS X admins need to take the same security steps as everyone else.
Sounds pretty smart to me...
Black Tuesday - Patch'em if You Got'em
Make sure you get the XMLHTTP patch. Also, make sure to deselect IE7 if you are waiting on that...
Also note that XP SP1 is no longer a supported platform. If you aren't on SP2 yet, then you can't patch.
Get a full rundown on the released patches over at ISC.
Happy Tuesday.
Phishing Kits Banned by UK's new Fraud Act 2006
A new anti-fraud bill has been passed into law for England and Wales. The Fraud Act 2006 received Royal Assent last week and will come into force in early 2007.
The new law aims to close a number of loopholes in preceding anti-fraud legislation, which the Government said was unsuited to modern fraud.
Until now there has been no single, general fraud law in English law, but an untidy mess of eight specific statutory crimes, such as 'obtaining property by deception,' and a vague common law offence of 'conspiracy to defraud'. Scotland does have a common law crime of fraud, committed when someone achieves a practical result by a false pretence.
The Fraud Act introduces a general offence of fraud which can be committed by false representation, by failing to disclose information or by abuse of position. The offence carries a maximum sentence of 10 years' imprisonment.
Hopefully they aren't forgetting about the security researchers that might have a phishing kit or two. I think I have one somewhere on my computer from the PIRT team.
Monday, November 13, 2006
RumorConfirmed: Sun Makes Java Open Source
Sun Microsystems Inc. said it will offer Java for free to widen distribution and adoption of the software platform among developers and companies using open- source technology such as Linux.
Java is being distributed under an open-source licensing plan that lets developers view and modify the software and also distribute it for free with other open-source technology, Santa Clara, California-based Sun said in a statement today
Sunday, November 12, 2006
Rumor Mill: Sun to Open Source Java under the GPL on Nov 13th

No, I'm Not A Doctor -- But I Can Search Google
A new study from a group of Australian doctors says that Google can help doctors diagnose tricky cases.
It's hard to know exactly why they needed a study to figure this out -- it would seem like doctors would be pretty familiar with searching reference materials if they needed help making a diagnosis, and given the wealth of knowledge that's online, as well as instances where it's proven helpful to doctors, you'd think they'd have figured it out by now. But perhaps the bigger point is to emphasize the value of collective, shared knowledge.
One of the common retorts from critics of the likes of Wikipedia is that using it, or other internet sources, is like letting a crowd of untrained people perform brain surgery. That's patently false, and when you have a group of trained, intelligent people (in this case, doctors), that are able to pick out the expert resources from the unreliable ones, the crowd and its shared knowledge can be quite useful.
Of course, Google and the internet as a whole can be quite a boon to cyberchondriacs, and people who think they can diagnose themselves by looking things up online.
However, the internet won't replace doctors -- it just offers them a tool to supplant the Physician's Desk Reference, medical journals and other more traditional resources.
Vista RTM "Partially" Cracked by Pirates Already
Well, so much for closing piracy loopholes! With Windows Vista and Office 2007 only just going Gold, and not even available to Microsoft beta testers, developers or volume licence subscribers, the first cracked versions have already hit the pirate boards.
The Windows version which has been released is called Vista BillGates. It doesn’t feature any activation cracks itself, and the supplied product key is just for the installation.
The activation crack is a separate download, and works by replacing the licensing components with components from beta builds. Then using a product key from Beta 1, Beta 2, RC1 or RC2, the Gold version of Vista can be activated online.
Saturday, November 11, 2006
Hacking Firefox Extensions to Work with 2.0
After a bit of reading, I found that it will work if the extension is modified a bit. So I asked my friend and Firefox theme creator, Aaron Spuler, for a little help. He told me about a simple modification that I could do in seconds. Here is how it worked....
1) Download the XPI file and open it with WinZip or WinRar (or whatever you use). Extract "install.rdf" and open that file with WordPad.
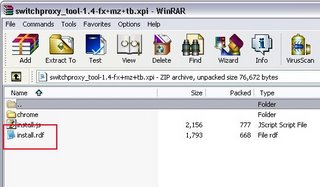
2) Modify the "maxVersion" variable from "1.5.0" to "2.0.*". As far as I can tell, you only need to change the first set, but you might need to change all three sets.
Original
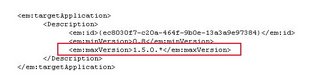
Modified

3) Save the file and copy it back into the XPI file (overwriting the original file).
4) Install the Extension into Firefox, restart and test.
Now this works for Swtichproxy, but this will not work for all extensions. Firefox did change APIs and other things since 1.5, therefore other extensions may need to be re-coded work correctly.
Perfect Blogger has two other methods that work as well.
It's a Silly World
Aussie beef cattle enjoy a relaxing bottle of red
SYDNEY: A glass of red wine traditionally goes well with a steak, so at the behest of a top Japanese chef an Australian company is adding wine to beef - while it is still on the hoof.
Each animal gets about a liter of a fruity cabernet shiraz merlot mixed in with its feed each day for 60 days, company director John McLeod told the Sydney Morning Herald.
The idea was proposed by Japanese celebrity chef Akio Yamamoto, who suggested that Margaret River Premium Meat Exports followed the example of the Japanese producers of famed Wagyu beef, who pamper their cattle with beer, massages, and music.
"It's quite a good drop actually and they tend to eat more than they should so I guess they like the taste.
"The antioxidant properties that we associate with red wine appear to have an effect on the meat's color and shelf life, and from the tests we carried out the meat also tastes sweeter."
Keeping up with the Joneses
LONDON: More than 1,000 people called Jones gathered under one roof to break the world record for the biggest get-together of people with the same name.
Some 1,224 Joneses packed into the Wales Millennium Centre in Cardiff, smashing the previous record gathering of 583, set by the Norbergs of Sweden.
Guinness World Record officials had the task of keeping up with the Joneses and validated the attempt, after people with the Welsh surname descended from as far afield as Australia and the United States to take part.
Grace Jones, the flamboyant Jamaican-born 1980s pop star and former Bond girl, was among the famous Joneses entertaining their namesakes at the theatre.
Designer naff is the new cool, says 'Vogue'
LONDON: Designer naff, from kebabs, diamante, and fluffy slippers, will be all the rage in the New Year, said the British edition of style bible Vogue in its December issue.
Package holidays, jelly shoes - a 1980s favorite of little girls - and even hamburgers have been redesigned to become chic, it said.
"Cheap and cheerful favorites are going up in the world. The buzz phrase is 'upmarket-downmarket'," Vogue explained.
Designers have turned their talents to tacky items, reviving the fortunes of all things tasteless.
Kebabs, often a late-night staple food for vomiting British drunks, need to be salmon shish to cut it with fashionistas, while hamburgers get the nod if they are made using ultra-pricey Wagyu beef from Japanese cattle fed on grain and beer and regularly massaged.
Fluffy slippers can be cool, as long as they're sheepskin.
And Louis Vuitton has created jelly shoes for £160 ($300) per pair as "the naff seaside staple hits new fashion heights."
Eunuchs an effective weapon against India tax evasion
NEW DELHI: Eunuchs in eastern India were drafted by authorities to sing outside the homes of tax evaders to embarrass them into paying up, a report said.
Sari-clad eunuchs turned out in force alongside local tax collectors this week in Patna, capital of Bihar, India's most lawless state, the Indian Express reported.
"Pay the tax, pay the Patna Municipal Corporation tax," chorused the eunuchs on the doorstep of their first target, Ram Sagar Singh, who owed Rs100,000 ($2,240).
A mortified Singh promised to pay within a week, the report said.
Toronto wine cellar in the sky creates a buzz with new world record
TORONTO: A Toronto restaurant in the CN Tower claimed a new world record this week for the highest wine cellar. It prides itself on having 9,000 bottles stored 351 meters (1,151 feet) above ground in the world's tallest structure.
"It's pretty high," said Guinness World Record keeper Carey Low, who was sent to verify the claim to fame.
"I don't think this record will ever be broken," he said. There are taller buildings now being constructed elsewhere but I don't think they have plans for a top-floor restaurant or wine cellar."
The European-style wine cellar at 360 Restaurant was built in May 1997.
It resembles a typical underground wine cellar, with cedar racks and cherry doors. It features more than 550 labels from around the world that sell for anywhere from C$40 ($35) to C$3,000 for a 1993 French Burgundy.
